Cyber Security Infrastructure, AI & Semantics
A Human Centric Approach
DOCUMENT STATUS: 23rd September 2019 — second draft
An article in forbes today speaks of The $100 Trillion Opportunity: The Race To Provide Banking To The World’s Poor.
As is distinctly defined by me, i believe they mean a knowledge banking sector, but if we can’t get it right here — how can we expect to help make it work elsewhere.
The $100 Trillion Opportunity: The Race To Provide Banking To The World's Poor
_T wo years ago, Amylene Dingle lived with her husband and 7-year-old daughter in Payatas, an impoverished Manila…_www.forbes.com
ABC Footage from my Conference in 2017, featuring 2 of its speakers. Other footage can be found here including the 1 hour intro i produced Christmas Day 2016.
There is a long-incubated capacity to vastly improve National Cyber Infrastructure capabilities by providing civilians ‘knowledge banks’. AI empowered informatics services that provide our society the means to operate domestic infrastructure, better equipped to respond to emergent threats.
This article reflects upon a topical pursuit that has incorporated a great deal of work, over many years, within an exceptionally nominal domestic budget availability. In so doing, this article is a response to the “Australia’s 2020 Cyber Security Strategy: A call for views” made available online, as noted below, yet in many ways — this extends upon the concepts communicated in the video, i produced back in 2016, per below.
Fast forward a few years, in a recent article: “Exclusive: Australia concluded China was behind hack on parliament, political parties — sources” — the following statement is cited;
On a visit to Sydney last month, U.S. Secretary of State Mike Pompeo delivered thinly veiled criticism of Australia’s approach after Foreign Minister Marise Payne said Canberra would make decisions toward China in based on “our national interest”.
Pompeo said countries could not separate trade and economic issues from national security.
“You can sell your soul for a pile of soybeans, or you can protect your people,” he told reporters at a joint appearance with Payne in Sydney.
Source: reuters
Exclusive: Australia concluded China was behind hack on parliament,...
_SYDNEY (Reuters) - Australian intelligence determined China was responsible for a cyber-attack on its national…_www.reuters.com
Today, there is a lack of cyber-infrastructure to safely provide individuals cyber-infrastructure that is legally and technically defined to be operated for individuals. Nonetheless, technical solutions to support a better ‘digital identity mandate’ does exist, and the broader question becomes — how can we form appropriate PPPs to build this critical cyber-physical infrastructure?
Can we do so using bot model methods as to deliver a commons cyber infrastructure outcome?
The question is not whether there is an opportunity to build infrastructure that’s, going to be worth an enormous amount of money, but rather,
what is the most ethical method, to build it.
How can cyber-security methodologies work to ensure the activity of human thought — does not incur any ‘unnecessary expenses’; ‘subscription costs’, that may be built into cyber-physical systems and become an underlying cost of life. Cyber Physical Infrastructure must value human rights, the right to be alive, and to meaningfully support our biosphere. The right to learn languages, and the means to make best efforts to ensure when a person transfer funds (ie:$5) the recipient gets the amount transferred (ie: $5). To achieve these sorts of outcomes, Cyber Security policy must acts to lower the threats IP may otherwise cause, and ensure what does exists, supports life, dignity and ‘rule of law’.
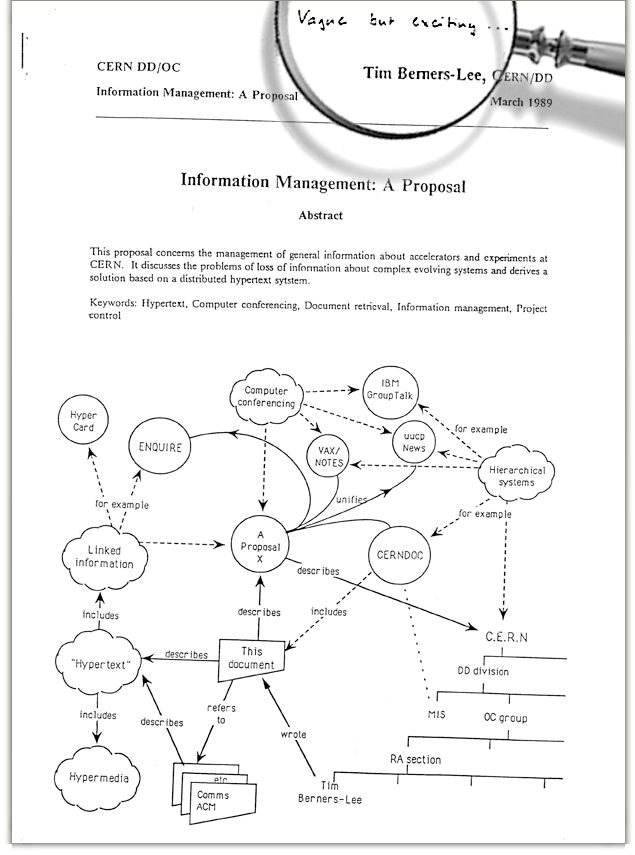
CERN Proposal for the Web
I have previously drafted articles (often still draft) providing ecosystem related notes about the opportunity to create a different type of informatics management system. The concept of an ‘informatics management system’ is similar to the idea of an information management system (ie: WWW — the world wide web); although the differentiation between informatics and information, is that informatics also refers to the manner in which information is processed.
There is a rise of cyber-native agents, software agents often called bots or AI. The World-Wide-Web was built to a framework that was built to support ‘Artificial Intelligence’, working with DARPA led DAML Researchers, the objective constructs of the Semantic Web was thereby commence from around ~2000. These tools now power the world-wide-web.
This article seeks to address notes for cyber security considerations; noting some aspects have been previously addressed in my article about Comms & Security: Privacy vs. Dignity. My works led to building works upon semantic web tooling from around 2010, due to the patent-pool structures and related IP infrastructure environments. This in-turn led to knowledge about web-science principles, which extended earlier ideas about the blending ‘liberal arts’ and computer sciences; as i worked to define and illustrate the opportunity to produce ecosystems for a knowledge age that is most simply illustrated using diagrams on my article Inforgs & The Collective Infosphere.

Image Source: Twitter — Dame Wendy Hall the ‘Mother’ of Web Science
Eben Moglen is a professor of law and legal history at Columbia University, and is the founder, Director-Counsel and Chairman of Software Freedom Law Center. As is illustrated in his presentation at Re:Publica 2012 (excepts below) existing capabilities of this technology, as illustrated by ‘the search box’ highlight technical capabilities built-into our web today.
Excerpts from: Eben Moglen in his presentation at Re:Publica 2012
The solutions; i now therefore discuss, and the related practical architecture frameworks, require government infrastructure to provide foundations in the interests of citizens, as independent & ’linked’ stakeholders, in our democracy.
The methodology sought to be employed; is built upon legal entity modelling, that relates the operational and personhood characteristics of legal actors to a permissive structure for the cyber curation of assets and capabilities on a societal wide basis. In so doing, this very different ‘information management systems topology’ provides enhancements for the meaningful benefit of all parties who rely upon ‘sense-making’ apparatus.
Our system of democracy, our system of government requires cyber infrastructure, In-order to support effective government in our modern cyber age.
It has now become imperative for sovereign governments and citizens who are to beholden them (and visa-versa); to make available capabilities they need to support cyber sense-making foundations, for useful employment for pragmatically progressive decision making practices & methods, that have a causal role in the future of self and others.
We are living in an age where the lives of natural persons is increasingly saturated in data, built to be coupled with analytics systems; that in many cases, are in-turn operated in the commercial domain, internationally. These infrastructure services define the mechanisms that support sense making capabilities, world-wide.
The evolution of this infrastructure will of course, continue on. Yet what I suggest; be seriously considered as a nation building exercise, is to invest and instigate the delivery of entity infrastructure, for artificial intelligence systems.
Our nation will increasingly depend upon informatics curated by entities, empowered by AI. To ensure this is ‘fit for purpose’, the informatics ecology should be coupled to all legal entities; both as independent entities; and as, constituent members to others graphs; inclusive to legal personalities, and their knowledge based capital ecosystems.
A problem that appears to exist today, is that the level of comprehension about these technologies and how they are able to be made to work in the interests of our democracy, is low. There are many unfounded assumptions that seek to purport the ability to produce infrastructure for natural persons, cannot be made. This is either a dishonest stance, or one that is built upon a lack of understanding.
To resolve this disabling ‘communications breakdown’ that acts to inhibit judicious, sovereign works; a methodology is considered necessarily required as to address emerging issues, and deliver solutions.
Should this assessment be considered to have merit; then the next issue, is how to scale rapidly.
One way this might starts by forming an appropriately equipped shared infrastructure; that can act to,
- Support a process of uplifting situational awareness; as to,
- Ensure informed decision making is made viable.
To achieve this;
- There are a multitude of subject matter expertise related disciplines required, to converge and form a strategic communications platform; as required to (Re-)define scope of works.
This outline seeks to prompt suitably skilled participants, with a specified form of ‘options statement’; that is sought to be processed, considered and made able to be assessable by others; on the basis of its,
- Underlying merits, rather than any other factors that ma act to discriminate; as to,
- form assessment of its underlying requirements analysis needs; and related considerations,
- that can be appropriated as to act in the interests of our system of democracy.
The underlying technical problems; include,
(noting, by ‘technical’ i use the term in a cross disciplinary manner)
- The vast majority of societal leaders appear to have nominal comprehension of how internet works; and its tooling (per above).
In-order to dimension the scope of these proposed discovery and opportunity analysis sessions, I am using the questions posed in the “Australia’s 2020 Cyber Security Strategy: A call for views’ document; made available https://www.homeaffairs.gov.au/reports-and-pubs/files/cyber-security-strategy-2020-discussion-paper.pdf as a primitive method to illustrate fundamental objective views that may be considered.
The basic premise that informs the responses to these questions, is predicated upon the discretionary decisions by government, to define legislative apparatus that would support a regulated industry of providers, serving the informatics needs of Australian Citizens; as to produce,
The foundational infrastructure for our Knowledge Economy.
The intended purpose of seeking government to do consider these objective requirements; is intended to provide materially required governmental support, in service of our System of Government, and the lawful acts of its agents.
noting therein;
The functional characteristics of ‘semantic web’ infrastructure delivers accountability frameworks no-matter how they’re delivered. The purpose of a ‘human centric’ approach, is to ensure accountability for wrong-doings is associated to human(s) and ‘rule of law’ associated in a jurisdictionally inclusive manner. Unlike the methods employed by online services today; where ‘terms of service’ declare via international contracts ‘choice of law’ in relation to the storage and operation of data, informatics & AI on a foreign basis; the methodology employed by this human centric approach delivers domestic alternatives, as to support the interests of citizens and citizenship.
Choice of Law ‘terms of service’ map — for major websites today. NB also — Map of largest websites
Distinctions can be made (provenance & graph analysis) between those who wilfully engage in wrongdoings as to cause others injury; and those whose actions cause injury, but not as a consequence of wilful unlawful behaviour (causality, inferencing, knowledge, ignorance, kindness, abuse, mislead, knowingly, etc.).
The technology based method is specific in nature, and whilst they power WWW today, the biggest problem appears to be its international governance.
Beyond the ‘internet’, the core infrastructure, Data / Information / Knowledge infrastructure services, inclusive to AI capabilities; are now governed globally.
source: wikipedia, liberal arts
To resolve this “problem”, alternative methodologies are need to be made interoperable with international internet based service infrastructure; engineered to support the needs of citizens and relations between them.
This undertaking is not simply about software, but moreover an activity framework that is correlated to the concept of web-science. Whilst there is no known Web Science Degree or course offered in Australia, the underlying method is about blending the liberal arts with computer science tasks, as I discussed in an earlier presentation from 2013 about this body of work, back then.
Whilst existing infrastructure solutions perform many of the technical functions well-enough today, it is the means to re:engineer the business systems functions that is of most importance overall. The underlying body of work that i refer to in my responses below, has produced the tools to do so.
Tim Berners-Lee demonstrating ‘solid’. Nb; @~1:18 — i’m ‘timo holborn’ as displayed as one of the 36 names, in that list (noting — i know some others not shown there).
Whilst this progress has many attributable relations to it, i highlight the fact that in 2014 MasterCard provided a $1M investment, which provided the means for Tim Berners Lee to start work. This has now evolved into inrupt, which is in-turn an illustration of foundational works, designed to work with other critical components; that are amongst the key projects i’ve been instrumentally involved in, since i produced the proposal works[1] talking about ‘knowledge banking infrastructure’ [2] before finding others worldwide, as a consequence of requiring ‘patent pool protected’, royalty free standards. Therein, i would like to also note the works of Henry Story that include, but are not limited to — his work on a ‘web of nations’.
From Digital Sovereignty to the Web of Nations
_This blog post follows up on Epistemology in the Cloud — on Fake News and Digital Sovereignty presented at The Web…_medium.com
A practice method i had learned about earlier, due to IPTV related global works.
Therein, imho, provenance — is really important; as is telling the truth.
If we build an economy upon unstable foundations, our means to manage security threats will be negatively impacted, whilst simultaneously benefiting others elsewhere in the world as a consequence of sense making vs. reality, in a world where societies are made to work, with artificial intelligence.
1. What is your view of the cyber threat environment? What threats should Government be focusing on?
My considerations about the underlying threat analysis is that the greatest threat is one of institutionally engineered governmental irrelevance, as to result in significant and sustained additional economic harm, by international forces.
It is pragmatically of great substance, that government workers may do great harm to Australian Citizens on the basis of assumptions (or wilful negligence / malfeasance) whereby the tooling produced to operate governmental entities become designed in such a way as to undermine ‘good, operational hygiene’.
It is difficult to maintain ‘good hygiene’ of a group entity (persona ficta) that is dependent upon the activities of natural persons (natural legal entities / citizens) if the informatics systems about the private lives of citizens is solely able to be curated by international platforms (under external ‘choice of law’).
Every Australian worker (Agent of persona ficta) is firstly a natural legal entity who, most commonly as a citizen; are equipped with tools by our system of democracy to support their individual needs in the pre-cyber realm (ie: bank accounts, identity document & personhood characteristics, ability to create, store, own and make use of (legal) documents, instruments, facts of circumstance) independent to their employment related identifiers.
Yet this is not domestically the the cyber-realm.
There is sufficient information stored on platforms of informatics trust (ie: that a database entry & inferred information in a platform is trusted to exist or not exist, on the basis of inspection) on international platforms to correct false assumptions. These systems are becoming increasingly pervasive.
A problem is; whether or not support for ‘rule of law’ is built into the cyber-physical (and legal) systems being produced.
‘Artificial intelligence’ (‘AI’ ecosystems) infrastructure is increasingly influencing society, and increasingly pervasive in nature. As is an implicit constituent of principle functional design, these systems form declared ‘inferences’ which in-turn associate to actors and their agents.

AI Ecosystems infrastructure incorporates data systems, that consume information in a programmatically defined manner to form ‘knowledge infrastructure’ services.
Thereby being more than simply data or information, as embodiments of ‘knowledge’ produced for specified purposes by organisations in utility of the ‘wisdom’ defined by people.
Knowledge systems incorporate ‘data’ that is in-turn is employed to form an array of artefact related inferencing suppositions; ranging from sentiment analysis (ie: good actor / bad actor) through to other asserted attributes and outcomes. Today the vast majority of ‘consumer platforms’ store and make use of ‘consumer data’ by way of terms of service agreements that are internationally based both for ‘consumer data’, applications and the AI capabilities produced as a consequence of operational license to employ consumer data for commercial purposes (to build new AI capabilities).
It seems improbable that nations of the world will find these terms acceptable into the foreseeable future.
Yet, the probability the USA will alone resolve these problems, appears to be, in my view, quite low. Indeed there appears to be difficult legal circumstances that act to inhibit their capacity to do so.
Whilst it is in the national interest to ensure they’re able to undertake transformational activities, their means to do so, in isolation to external (good will) influencers, faces inexorable challenges.
This is a global problem that has been brought about by the legal methodology employed by silicon valley leaders. It seems improbable, that this will be left to be ‘status quo’, without any form of recourse or improvement / improved functional support, by some form of means.
As to address the underlying problems; There is a clear and present opportunity to build and make available domestic infrastructure which in-turn requires nation building strategic funding.
A series of strategic initiatives well executed, can solve these problems and there is enormous opportunity that is available for those who perform leadership activities as to deliver solutions. To do so, any such leading US partner for international works would need to understand the opportunities.
The question that this then brings about is;
- Where (in the world) will this be stimulated & curated from; with the trust of stakeholders, internationally, working to deliver peace via a newly minted framework, for global socioeconomic social order supportive of, rule of law.
- Is it expected that Australian entities should be able to bring to market solutions without the meaningful assistance of the Australian Government? If so, how is Digital Identity made to work?
2. Do you agree with our understanding of who is responsible for managing cyber risks in the economy?
Somewhat. There is a problem; whereby,
The ability to represent the interests of natural persons; particularly where distinct from those of the interests (ie: in the context of wrong-doing) of a legal person (inc. Government), as is sought to be prosecuted to best effect by executive and administrative agents of said legal personality.
Part of the problem today appears to be grounded in the consequence of todays corporations act and the capacities it provides directors to consider the human rights related obligations & requirements, for themselves, their children, their friends, family & others.
Therein, the conceptual consideration in relation to consequence of a bad agent (employee / resource) rather than that of an ‘autonomous act’ by a legal personality (ie: company) to wilfully seeks to engage in wrong-doing as a consequence of its own and independent acts; without the meaningful assistance or fiduciary responsibly of its agent(s) — is unclearly defined and/or supported.
In almost every instance of wrong-doing, human actors are involved irrespective of employment status and/or employer.
Rule of law should not be undermined.
What appears to be the consequence of wilful decisions today, has resulted in a circumstance where the means to present and prosecute the requirements for humanity is now quite hard to achieve.
There are incidents of information being required in a timely manner, that is not afforded due to ‘business systems’ or that actors are provided ‘false and misleading information’ as to influence others, in a manner devoid of accountability; whereby the subjective rationale is that the data-subjects record be not shared as to preserve their privacy.
These curated means act undermine Human Dignity, which is particularly problematic where international systems can identify wrong-doings.
Where these sorts of behaviours lead to harm of the ‘data subject’; the consequences include those of causing injury and a failure to protect that persons human dignity.
Therein; Amongst the many problems, commercial actors (and even non-profits) seek to obtain long-term income generating potential, as to serve the duties of their role as agents, as is amongst other things; a constituent and tangible intepretation of the duties bestowed upon directors by way of the corporations act.
Additionally; rule of law principles include the legal concept that
‘All people are presumed to be innocent until proven otherwise and are entitled to remain silent and are not required to incriminate themselves.’
Therefore, if only one (type of) legal person is entitled (and/or required) to store trusted records about a circumstance, then this can act to work against the broader series of principles outlined by such principles. Government and government departments; by way of their agents, may themselves — in-turn, seek to employ such measures as to protect themselves from litigation / accountability for (intentional or unintentional) wrong-doings.
So, how is quorum achieved on a domestic basis, if the tooling provided for civilians, is delivered by way of international law, services and governed intellectual property agreements?
Should changes be made; how can the existing ‘knowledge infrastructure’ (inclusive to those that relate to significant acts of wrong-doing, particularly on a systemic basis) be appended?
Consequentially,
I fear the definitions of what is suggested by this question — is predicated upon what the government (or the departments) view and/or understanding is today; that does not clearly communicate knowledge of the works both here and abroad; as to encapsulate a formal informed response of the proposed solutions framework, i am putting forward.
As such, my submission relates directly to why traditional ‘information management systems’ are not necessarily continued to be built upon.
As such, the assumptions made by those charged to make key decisions based upon their situational awareness of what opportunities do pragmatically exist, to choose from..
May, as i otherwise speculate, require new briefing materials…
If it were the case, in reality, that no sophisticated ‘semantic web’ infrastructure existed and the only options available were those that relied upon traditional relational database technology; then the question posed, would be (reasonably) considered on an entirely different basis. However, in reality — that’s not the case; irrespective of any lack of technical skills and/or due-diligence capacities that may act, with great misfortune, to suggest otherwise.
Amongst the greatest of barriers that exist; the most significant ones are those of social issues, whereby leaders in various technical roles today do not know about semantic web, haven’t learnt it, don’t have business systems that support its use; and so, act as though their in a vacuum, to stop any works that may be brought about that is feared may act to disaffect them personally.
Cyber risks, whilst nuanced from physical risk ‘conceptual frameworks’, are no less harmful to any legal actor. What is harmful in any circumstance, is a lack of available pathways for timely and trustworthy legal response and the availability of legal remedy.
If someone criminally enters your house and harms its occupants or breaches an intervention order or steals your passport, or your phone; we’re told to call the police as the legal means to seek safety.
If they attend when this occurs they would likely act immediately. If they know where those people are, they would act immediately. Those performing the crime are not entitled to prevent a lawful search by seeking to protect their privacy, yet those employed by government to do the search must do so lawfully.
Yet if, someone enters and leaves the premises prior to police arrival, police may ask ‘do you have any evidence’ even if the wrongdoers had their phones in their pockets whilst committing the offence.
If someone harms you using database platforms — not much the police will do about it, particularly if action is sought in a timely manner.
It is a fairly unacceptable risk to government, that foreign agents understand both; how citizens have been harmed by their own government; and that those who do, may be ‘made use of’ by foreign actors as to drive economically disadvantageous (from a domestic perspective) agendas.
Whether these acts can be considered to occur ‘in bad faith’ or ‘as to manage risk’, is amongst the sorts of broader issues that are seemingly too complex to consider or form an educated stance on. A greater focus on human dignity, over and above the purported extension of ‘privacy doctrine’ as has evolved from OECD works in a previous era, could improve cyber security capabilities for Australians.
The role of citizens is far more than simply seeking ‘consumer protections’, with fewer lawful rights and capacities than would otherwise have been available to them, should dignity prevail. Every ‘consumer’ is also expected to do their best to be a producer, or a contributor to our society, our democracy.
By labelling natural persons ‘consumers’, the tools to do so are stripped away.
The instrumentation of international vendors is enormously sophisticated.
It is unclear how well these factors are brought into consideration as critical decisions are made here, and whether / how any such decisions made irrespectively, support or promote foreign agendas.
So, the circumstances appear that CyberAU is poorly supported today, at great expense.
The manifest responsibility of resolving this issue is that of its citizens whose needs, irrespective of their role (inclusive to those in government) requires foundational support.
To achieve this, the assessment of what it means, by business systems, to be a citizen; and what infrastructure is required for citizens, as we transition from the ‘print age’, to ICT knowledge systems alternatives is a very important set of tasks.
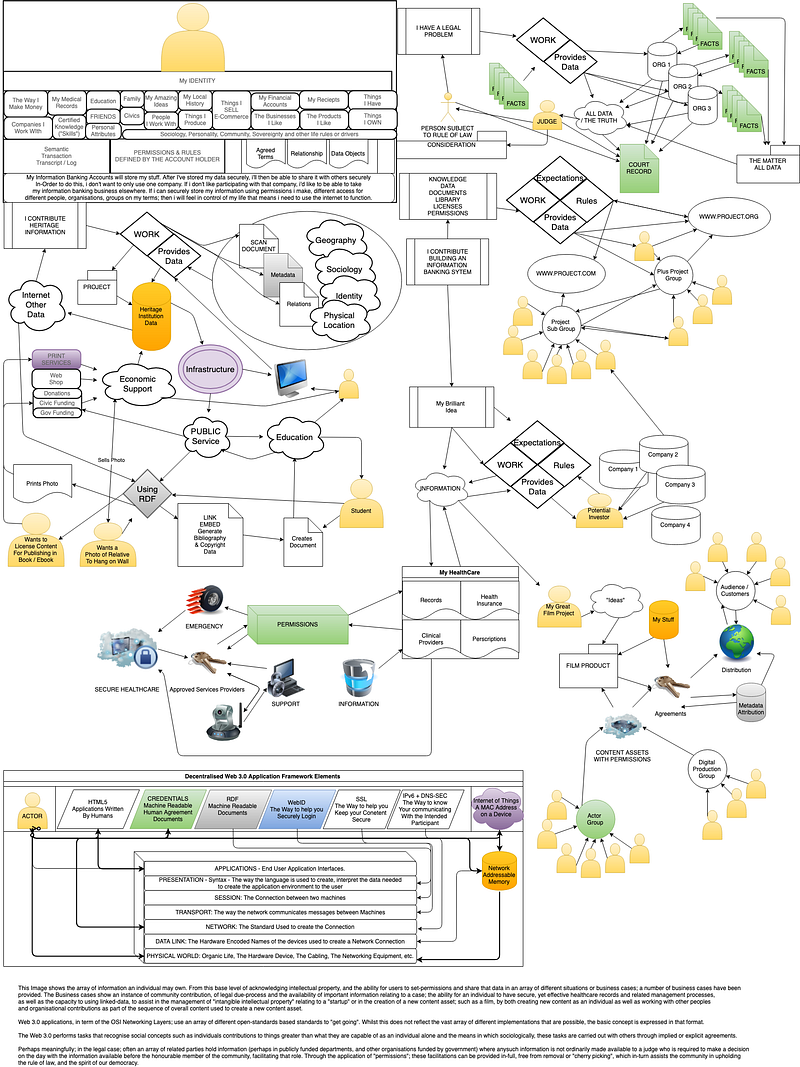
Diagram produced circa 2013–6 — note others here
This practical process is not just about how ‘evidence’ was accepted by a court in historical context; but moreover, what the burden of proof is today; and what exists ‘somewhere’ to support it. Therein, there are philosophical questions that need to be asked about the ideology of how these systems are designed and whether they’re intended to support ‘truth telling’ (non-fiction) or something else that will have known distortive characteristics (fiction).
How can ‘those trustworthy data’ things that exist ‘somewhere’, be better affiliated to law and related principle (ie: rule of law) via entity analysis & information management systems innovation procedures, as to get the best practical & tangible outcomes; both domestically and internationally.
Conversely, what are the factors that are inhibiting our national capacity to do so; and how should those factors be responded to, given, it is quite likely that said actions contribute towards great threats upon our national security, our democracy, our rule of law; and the basis upon which people may be gainfully employed by government in any dutiful & honourable role of public service.
3. Do you think the way these responsibilities are currently allocated is right? What changes should we consider?
I’m thinking my answer to this question is kinda no, although, its a complex field, that underneath the various aspects of complications — is built upon an existing body of law, that protects us all.
If there is no capacity to support the ‘civil tenant’ how could gov get it — right?
The problem today is that there is enormously diminished levels of support for the civil tenant both as a consequence of the introduction of cyber-physical systems. This is a consequence of ‘design frameworks’ that have acted to define what legal concepts be considered, as to be supported, by the implemented functionality produced in those systems; and those, considered by project officers to be deemed ‘out of scope’.
The implication is that there is no ‘safe’ domestic infrastructure services framework for natural persons to store and employ AI; with records such as,
- ‘machine readable — point of sale receipts,
- payslips,
- medical records,
- history of works
- security tokens for IoT Devices
- conversation history; and,
- other logs and the many other things that can be employed with AI by the beneficial owner of those informatics resources.
For the most part — the tooling that’s been required for citizens has been made overseas; and sophisticated ‘legal personalities’ have in-turn solely focused on what it is their agencies require.
IMHO — This should be radically changed ASAP.
There is a technical capacity to produce an alternative market-based offering, that in-turn would require laws to support — what i call — a (fiduciary) knowledge banking industry, that could be built upon standards based technologies.
Without the option for ‘consumers’ (citizens) to make use of this kind of infrastructure (or the means through which law may apply differently, to existing global silos); today, often this leads to a lack of capacity for those agencies to do a ‘fit and proper job’; which incurs expenses that would otherwise be unnecessary; alongside an array of other ‘unwanted effects’…
Inclusive to means that may better support the APS Code of Conduct, which in-turn may provide significant improvements for public trust of government.
The way cyber-infrastructure is operated today may be thought of to be similar to an idea of having ambitions for a financial sector without laws to provide or protect the capacity of civilians to independently (as natural persons — citizens) ‘own’ bank-accounts or property (homes / shelters).
In-turn, i believe the result is an array of unnecessarily engendered cyber-security threats; such as,
- A Lack of capacity for individuals to store important records (domestically)
- Lack of capacity for individuals to be easily subject to enquiry & means for self-defence (domestically — people can talk about problems in US platforms like facebook, but it won’t do much to help the innocent / those victimised by others who’d be subject to lawful repercussions)
- Lack of National Capacity (domestic) to make sophisticated enquiries, at low cost
- Lack of National Capacity (domestic) to retain Intellectual property for socioeconomic gains
- Lack of National Capacity (domestic) to evaluate complex circumstances; and stem the flow of unnecessary expenditures on triaging problems that have evolved; rather than addressing emerging issues early on (as to improve economic efficiency and cyber-physical security).
- Inability to form business models for persons who’ve been wrongfully harmed in the pursuit of positive economic (domestic) outcomes; leading to economic weighting issues between ‘good’ and ‘bad’ actors and the derivative benefits made accessible by either ‘class’ of ‘actor’.
- An Inability to produce globally interoperable ‘web native’ payment instruments to support economic growth; in many areas, including natural disaster mitigation & innovation.
- In ability to ‘cleanly’ (& Assertively) resolve issues (& threats) that may impact national security, involving (important) persons; alongside those of significant public expense and detriment caused by Defective Administration.
4. What role should Government play in addressing the most serious threats to institutions and businesses located in Australia?
The role of advancing the purpose, shape and doctrines relating to the operational purpose Government have evolved over thousands of years. Cyber should not unstitch its role or redefine it. To simply the mind sphere in relation to how this question be most easily considered; there are two ideas that may help,
- The Digital Twin Concept; that each ‘entity’ has both a physical twin (the real-world entity) and a digital twin (the cyber-space or infosphere entity)
- That all legal entities need both physical shelters (homes, offices); and cyber shelters; therein, legal personalities have server infrastructure today that curates management of their knowledge based capital — which is like a ‘cyber shelters’ for their needs. ‘consumers’, or natural persons do not have this capacity or infrastructure available to them, on a domestic basis.
It is impossible to entirely decouple the (private) lives of natural persons (citizens) from any role they perform with a group (ie: company / persona ficta). As such, the ability to maintain the interests of these group entities is in-turn coupled to the ability provided to protect the interests of citizens.
Amongst the many characteristics; Australia’s system of government, our system of democracy, is distinct to other regions. International examples, are built upon their international frameworks; for example, the United States provides by law an entirely different legal construct to our own.
Copyright Clause
_The Copyright Clause (also known as the Intellectual Property Clause, Copyright and Patent Clause, or the Progress…_en.wikipedia.org
Alien (law)
_In law, an alien is a person who is not a citizen or national of a given country, though definitions and terminology…_en.wikipedia.org
Similarly The UK (and more broadly the commonwealth) forms many unifying concepts, yet regions throughout this ecosystem of participatory nation-states all in-turn have their own particular systems of laws, and civil protections.
Our charter
_The Charter brings together the values and aspirations which unite the Commonwealth - democracy, human rights and the…_thecommonwealth.org
Therein — what makes most sense, is to ensure there is the means to best protect institutions and businesses located in Australia, by ensuring protections for its operational capabilities — as are carried out by natural persons — are in-turn also able to be granted fair, reasonable, appropriate and lawful protections, by making best use of the technological capabilities produced by mankind.

Article 27 of the UN Universal Declaration of Human Rights.
Without this underlying infrastructure, irrespective of any misappropriated ideologically ratified debates suggesting the contrary; without the means to protect the rights of natural persons, legal entities become vulnerable to attack.
As such, the ‘role of government’ should be evaluated inclusively, whereas it is now the case that the term ‘persons’ incorporates both ‘natural persons’ and ‘legal persons’ in many legal instruments.
comments about the ‘role of government’ include those such as,
“Government has three primary functions.
It should provide for military defense of the nation.
It should enforce contracts between individuals.
It should protect citizens from crimes against themselves or their property.
When government — in pursuit of good intentions tries to rearrange the economy, legislate morality, or help special interests, the cost come in inefficiency, lack of motivation, and loss of freedom. Government should be a referee, not an active player.” Source: Milton Friedman
Bill Gates is quoted by FT when questioned about the role of government; as saying,
“The government has a vital role in helping to tackle these problems. The voice of poor people, the price of that marketplace is nil. So some non-bottom line activity, of which government is a big piece and which philanthropy is a small piece has to come in for all the things of that nature.”
The PEO defines the role of (federal) government in the following way.
The responsibilities of the federal government include:
- Developing national policy; for example, plans for managing trade, foreign affairs, immigration and the environment
- Introducing ideas for new laws or changes to existing ones (called bills) into Parliament
- Putting laws into action, through government departments
- Making important decisions on behalf of Australians, such as whether or not to send Australian troops to war zones
- Representing Australia overseas, through key spokespersons such as the Prime Minister and the Minister for Foreign Affairs.
The most illustrative framework i could find was via NSW Gov; which states,
The Federal Government
The Federal or Commonwealth Government is responsible for the conduct of national affairs. Its areas of responsibility are stated in the Australian Constitution and include defence and foreign affairs; trade, commerce and currency; immigration; postal services, telecommunications and broadcasting; air travel; most social services and pensions. The Federal Government is also involved, mainly through funding, in many things largely carried out by the States, such as health, education, environmental issues, industrial relations, etc.
State or Territory Government
Under the Australian Constitution, the States are responsible for everything not listed as a Federal responsibility. However, sometimes both levels are involved. Major State responsibilities include schools, hospitals, conservation and environment, roads, railways and public transport, public works, agriculture and fishing, industrial relations, community services, sport and recreation, consumer affairs, police, prisons and emergency services. Each state has its own constitution setting out its system of government.
Local Government
(noting — i’ve slighted edited the original version)
Local Government areas vary greatly in size and character. State and/or territory areas are divided into cities, municipalities or shires, each with its own local council. The bigger country centres have city or municipal councils. Large but less populated country areas, with a number of small towns and large rural areas, are usually shires with a Shire Council based in one of the larger towns. The power of local governments is controlled by Acts of State Parliament such as the Local Government Acts. Local Councils are concerned with matters close to our homes, such as building regulations and development, public health, local roads and footpaths, parks and playing fields, libraries, local environmental issues, waste disposal, and many community services.

8 hour movement — as noted in previous post about web payment infrastructure.
As such — whilst market-forces may seek to ‘rewrite the terms’, as has happened before historically; as settlements were established internationally, ‘Cyber’ is in many ways similarly impacted by acts that are characteristically old in nature; irrespective of the nuances correlated to any specified example. In past eras, battles have been hard fought and won to preserve and/or enhance personhood; to abolish slavery (in all its forms) and to form international agreements to undertake trade ‘on fair terms’.
Yet therein; ICT now provides an ability to make use of labor sourced internationally without so much as providing an obligation to keep those labor resources alive, fed, sheltered or means to exist unto ‘rule of law’. As such, slavery in its many historical manifestations is different to web slavery, whilst still innately similar to the underlying moral issues faced by those who defined solutions to problems that were resolved before our time. Some further examples of this problem are illustrated in my post that communicates some of my research into the heritage of our economic infrastructure, whereby the relationship between resources (inclusive to human resources) and economics have always been a subject area of important works overtime.
Yet cyber infrastructure is essentially ‘sense making’ infrastructure, so if it doesn’t exist domestically as to revoke (or employ) the capacity to make use of ICT resources for sense-making, this has different implications to traditional slavery related practices.
In the old days, the owner or beneficiary of the slaves was required to maintain their ability to live and do the work. The beneficiary was not motivated to claim they did the work carried out by the slaves. Web Slavery is different, not only is it the case that the beneficiary doesn’t need to pay the costs incurred for maintaining the web-slave, but the beneficiary can also claim to have done all the work themselves. Therein, there is no need for recognition of labour, creative innovation, wrong-doings upon others — as they’re unlikely to have access to any evidence or funds as would be required by them to support their personhood and associations between them, and the concept of ‘rule of law’.
As such; the consideration about how our system of government requires ‘digital twin’ infrastructure, is an issue that spreads across all constituents of government (noting — AFAIK — constitution in Australia doesn’t make note of local government, as such, its powers are governed by state & territory gov).
As such, the means to ensure appropriate domestic cyber infrastructure, is required to be performed in a manner that is supportive of our traditional system of government, transposed online; in a manner that preserves separation of powers.
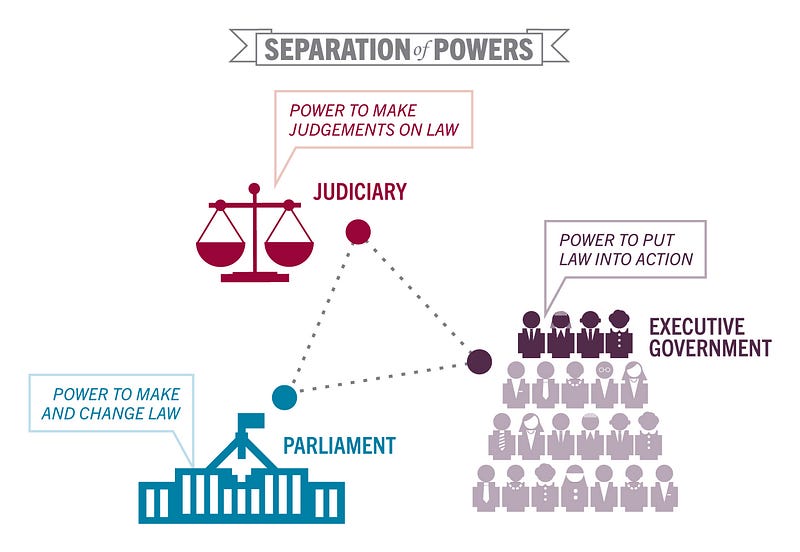
Source: PEO: separation of powers
To achieve this, people need to have the protected right to store and employ records that relate to them. In addition to this basic ‘data storage’ capability, extended means should be supported as to provide legal agents the capacity to curate how AI is used to communicate with other agents in relation to them. Today, this capability is very much in place for legal personality (companies, Gov), but this ‘situational predicament’ is not similarly the case for citizens.
As such, the works i have undertaken since 2000 predicated the establishment of what i first called an ‘information bank’ (pre AI) and later called a ‘knowledge bank’ and/or ‘knowledge banking industry’. By producing a domestic fiduciary industry, separation of powers is maintained; whilst significantly uplifting the means to support ‘rule of law’ and cyber security.
To achieve a situational position of this opportunity now being available, extensive international works have been carried out as to produce a technical opportunity to do so. This effort has not been matched by domestic (economic) infrastructure support and now requires investment to do so.
5. How can Government maintain trust from the Australian community when using its cyber security capabilities?
Tell the truth? Preclude government from being entitled to protect itself when its actions harm civilians? Act in a manner that makes use of technology to be more trustworthy than foreigners?
There are indeed many unfortunate yet understandable ‘simple answers’ for those most dedicated to seeking means to hear only a sound-byte, a paragraph or a couple of dot-points.
The real answer, imho, is that its not at all that simple.
The ability to communicate what a smart-phone is today, is far easier than was the case prior to the commercial availability of them. Therein, with respect to innovation pipelines; it is most important government be trusted to engage ‘on fair terms’, as such it’s not simply about ‘trust’, but ‘trusted to do what’?
The question positions itself as to suggest government currently retains a sufficient level of trust and confidence, in the manner it discharges its responsibilities, in a manner underpinned by fit and proper integrity measures that do not expose the government (or the people in its care) to risks.
Therein, an array of sentimental considerations relating to formed views associated to the consequential appropriateness of Compensation for Detriment caused by Defective Administration across many sectors.
Therein — perhaps, it could be a ‘consumer’ form that makes use of AI to evaluate existing governmental records, and automatically make payments in an automated manner. Yet this is tactically amongst the perceived problem. Present-day solutions appear to be to make legal remedy as difficult as possible to achieve. As a consequence of this, bad actors are flourishing and there are increasingly more ‘productivity enquiries’, ‘royal commissions’ and related works; which only act to protect wrong-doers, rather than to support acts of leadership that would undermine any potential benefit they would ordinarily obtain by wrong-doings.
As much as there are means to launch enquiries, royal commissions and related future remedial works; there is possibly also an opportunity to launch litigation businesses that could seek to exploit real-world factors, the Australian Cyber Security capability seems inept or unable to address internally, or otherwise.
Therein — what i am trying to communicate is that ‘good hygiene’ of government operations is indeed a national security infrastructure requirement. As such; the broader problem is, that the services infrastructure for citizens / civilians, is not currently made available for their beneficial use.
As a consequence the ‘canary in the mine’ is not domestic, but international.
Existing practices seemingly have a tendency to require additional government money, to shift liability caused through the misappropriated expenditure of government money, continually over a temporal period.
This policy related decision making practice method, exposes Australia to cyber security vulnerabilities by many, enumerate means.
What is required is an ecosystem of trust infrastructure, whereby the concept of trust becomes a form of reliable currency that is as trustworthy; and likely overtime, more valuable than any amount of money that may now be used for the purposes of establishing ‘trust’ or ‘trusts’.
To achieve this, the means for natural persons to “plant, grow, farm and harvest” trust assets within the cyber domain is of particular importance to us all; and by extension, both natural and national security, which is underlying all other things — socioeconomically built.
What this means in reality, is that our information age, or indeed any evolution to a ‘knowledge age’, is built upon what we do. If government policies act upon important and widespread social issues by limiting public information about it, such efforts have the effect of distorting the foundations required for public trust.
Unlike former eras and mediums of war (Sea, Land, Air, Space) cyber is different. Who ‘we’ control, or how it is that some, be provided means to exploit others, becomes irrelevant in internationally interconnected ‘information systems’, where, trust is about ‘who provides reliable basis to form opinions about reality’.
Perhaps an easier way to think about this could be achieved by thinking about the way Australians developed a sense of trust with our government, and how the world developed a sense of aspirational good will towards the USA post World War II.

Source: Declaration of Human Rights by Eleanor Roosevelt (Audio Available Here)
Therein, what were the core tenants, the core values that were portrayed, instigated and prosecuted by government in the interests of our nation and its people. Was there a relationship between the role the USA performed in defining, for instance, the UDHR with Australia and our status?
Are thee current practice methods designed to support the extension of these meaningful achievements by way of cyber-physical considerations? In 1945 the objective consideration by VANNEVAR BUSH in his article As We May Think, spoke about the activity goal, post World War II to define ‘knowledge systems’, not misinformation systems.
The goal was seemingly to produce apparatus that provided mankind the ability to act upon knowledge, not fake news, not to undermine ‘rule of law’.
In this vision (per video above) set-out in a short video narrated by the words of Thomas Keneally, one of the concepts communicated is that Australians should look to the law as a source of peace in every day life, is this truely the way our Australian Government is electing to make use of its cyber capabilities?
Sadly, there are many instances there are circumstances where the employment of cyber-physical systems are shown to exact circumstances leading to death, upon citizens. In my opinion also, the effective preclusion of the ‘civil tenant’ from being able to employ ICT capabilities to improve the circumstances of ourselves and others in our community is leading to other far broader problems, which are not able to be acted upon by the vast majority.
As such, one need only review at the circumstantial predicament for young people seeking to gain the knowledge and qualifications required to resource themselves with the capacity, to fully and to the best of their ability, contribute to the future of our society.
Universitas Doctrina et Sapientiae
_Re:defining the business systems for the tertiary eduction sector._medium.com
Suicide is known to be high. See: KMPG Report, APH Report, amongst others — whilst circumstantial (ie: major life events such as family separation) is more difficult to find online resources about generally, for various reasons?
Whilst this is currently being responded to by means that seek to extinguish acts of suicide; the underlying problem that presents a significant role for the ‘fit and proper use’ of Australian Cyber-Security capabilities, is in preserving the needs of Australians to preserve their sense of human dignity, as they otherwise seek to contribute to our nation and its role worldwide. Therein, the greater cyber-security & national security threats, are not born by those who act by harming themselves, but rather those engaged in harming others.
Where intentionally harmful acts are rendered meaningful service by government, particularly those carried out systemically, we fail as a society.
No matter a persons ‘state of mind’, wilful (or involuntary) acts, the means to build cyber-physical infrastructure that is equipped to promptly respond, requires domestic capabilities that support the needs of citizens. This inclusive consideration includes those of people who work in some form of role relating to government expenditure (public servants) in our system of democracy;
and related functionally supported / required roles that may fall out of the scope of formal requirements put upon others, and be used to exploit such oversights.
A significant problem today, is that irrespective of the way these capabilities are developing rapidly internationally; the capacity to advance our capacities, may be considered a threat to those who’ve engaged in wilful wrong-doings; seeking to retain impunity for their acts,
“curated acts, that act to push Australia’s socio-economic interests backwards.”
An image that portrays a Social Graph
Australia is built upon principles such as ‘rule of law’ which should be employed, as should the APS code of conduct be considered binding, increasingly ‘secrets’ do not exist and the ‘ripple effects’ are increasingly able to be mapped, not just in relation to acts that be put upon the poor; but moreover, any relationships wrongful acts have upon providing meaningful assistance to faculties of organised crime.
It is important all Australians are supported, on the basis that it be a critical function of government to ensure no civilian be made to have no rights meaningfully available to them for ‘lawful recourse’ or that that any idea of lawful protection and legal remedy, due to gov policies, be deemed mute.
To do so, is a particularly undignified and wrongful stance, given the present-day cyber-capabilities that are built into our lives, our environments and our ICT related devices. The means to uphold law, aids to improve our laws and in-turn furnishes our system of democracy core ingredients it needs to support our domestic sovereignty, safety and capacity to meaningfully engage others world-wide, upon a basis of our commitment to contract relations ‘on fair terms’.
It shouldn’t matter whether an Australian is rich or poor, the apparatus provided by society to enshrine ‘rule of law’ should support law & government, not crime.
If the tactical employment of our cyber capabilities are usefully employed as to wrongfully limit and/or act as to extinguish access to justice; the opposite, that is ‘wrong-doings’ becomes better equipped. More broadly, it is in the interests of our cyber security requirements that this situation be reversed and then built upon. To do so, it is not simply about technical innovation but also the means to innovate economic systems as to appropriate available support.
Today, there are instances of significant wrongdoing & curated acts of wrongdoing, yet no public statistics about issues that are well-known by subject matter experts. This indicates a level of tactical distortion, which is worrisome; particularly in circumstances where those aspects of life would produce stats as a consequence of mandatory gov payments and/or interactive engagements with gov as required circumstantially. Distorting reality, doesn’t make it go away. To think otherwise is something that can be called a dissociative behaviour.
There are many ways in which Domestic Cyber Capabilities (About Australians) can be employed for proper purpose and it would be optimal if our capabilities addressed issues — before international alternatives did so for us, as a consequence of our unwillingness to do so ourselves, in the first place.
Should this be materially reversed; I believe the means to radically redefine the relationship Australians have between our Australian Government and our experiences, our choices in life — can be improved, as would international sentiments and our capacity to improve ‘terms of trade’ worldwide.
6. What customer protections should apply to the security of cyber goods and services?
Ideally, the ‘choice of law’ provisions in relation to ‘the data’ of Australian Civilians should relate in-turn to their domestic framework of law; as to ensure concepts such as ‘copyright’ and ‘privacy’ are coherently relevant. Yet, as there’s about half of the 7.5Bn people on the planet using WWW, and the total make-up of Australians (inc. kids & elderly) is ~25 million, we may only by able to act as to help “international relations” with “thought leadership”.
As an example of how services are presently operated; please find current extract from the terms of service agreement provided by Google;
“The courts in some countries will not apply Californian law to some types of disputes. If you reside in one of those countries, then where Californian law is excluded from applying, your country’s laws will apply to such disputes related to these terms. Otherwise, you agree that the laws of California, USA, excluding California’s choice of law rules, will apply to any disputes arising out of or relating to these terms or the Services. Similarly, if the courts in your country will not permit you to consent to the jurisdiction and venue of the courts in Santa Clara County, California, USA, then your local jurisdiction and venue will apply to such disputes related to these terms. Otherwise, all claims arising out of or relating to these terms or the services will be litigated exclusively in the federal or state courts of Santa Clara County, California, USA, and you and Google consent to personal jurisdiction in those courts.”
now therefore;
my consideration & suggestion is, that as an Australian Citizen, i would prefer my data to be governed, by default via “Choice of Law [state | territory] in the Commonwealth of Australia” as i am a citizen of Australia, and by law i believe it is most likely that i be considered by US law an Alien.
Therein;
The rights of personhood, of personal human agency, as is in-essence attached to the concept of citizenship, as has developed overtime, should no reasonably be undermined on the basis that a person seeks to use tools to communicate.
Certainly the use of a pen & paper or vocabulary, didn’t come with such terms.
If the answer is to form a market-based-mechanism, then it appears most important to ensure there are comparable domestic alternatives available to those afforded upon the same personhood terms enjoyed by US Citizens for US Services.
Yet if more sophisticated international means were applied; then beyond the considerations of more simply adding ‘GST’; the simple answer is that there should be provided a means for civilians to obtain, store and independently make use of the derivative apparatus provided as a consequence of a consumer or sale event, socioeconomically, in independence to the provider of those (cyber) goods and/or services.
What this means (explanation for a lay persons); is that,
- There is a complication with online services provided freely in that ‘consumers’ are not considered to be ‘the customer’. Domestic ‘choice of law provisions’ relating to ‘consumer data’ should be available anyway.
- If a retailer sells a person a TV, then they should be required to offer the issuance of a digital (machine readable) receipt. This might provide them (and other supply chain participants) the means to have a machine-readable record of the device itself, and the ownership history of it. In-turn the operation of that TV device; should not require the consumer to send usage information to an international entity, as a requirement built into how that device is used.
Therein; the consideration are,
That there should be an alternative that is mandated to be required that results in ensuring alternatives are necessarily made to be available.
If required, an alternative may be, that there is clear consumer labelling on it.
Perhaps a brand — a bit like ‘Made in Australia’, it could be something that says ‘Aussie Cyber Compatible’ (Which would in-turn require high levels of trust, to be engineered).
Therein — the requirement for ‘consumers’ (citizens) to have the option of being able to obtain their own secure services is required prior to any such type of opportunity becoming at all relevent and the concept of ‘secure services’ does in-turn relate both to the legal and technical aspects of cyber products and services, some of which are becoming increasingly mandatory.
Whilst cloud-storage services commenced at around 2000; questions may be asked, ‘why now’ and why weren’t these problems sorted out before?
7. What role can Government and industry play in supporting the cyber security of consumers?
In-order to resolve the predicament of uplifting our existing cyber-physical infrastructure environment, as to bring about the availability of ‘fit for purpose’ alternative infrastructure solutions;
- There is a perceived requirement to produce cyber-security laws that target support for the needs of civilians; who would in-turn,
- Be therefore equipped to seek protection of those rights; on an independent basis,
- In any adversarial legal circumstance involving any other party, both domestically and abroad.
I have conceptualised this ‘capability’ as an (international) ‘knowledge banking industry’; which is considered to be,
- a form of cyber-infrastructure provider whose operations are subject to appropriate regulatory expectations and restraints;
which would include,
- The prevention of the infrastructure provider from employing consumer data for commercial purposes that are not expressly sought by the consumer
- The responsibility of the infrastructure provider to maintain ‘mandatory data retention’ and related legally required infrastructure provisions for (domestic) law enforcement
- A technical requirement to operate the informatics environment based upon open-standards as to ensure consumers are able to migrate their informatics environment (inforg) from one provider to another, without functional degradation of their environment
- A requirement for national certificate infrastructure to be established; and for local ‘knowledge banking services’ to make use of it, as Certificate Authorities (CAs).
- The requirement to make use of cryptography services to validate attributions that relate to submitted informatics (documents / digital assets) from consumers; as to provide,
- ‘Tamper Evidence’ and support for other evidentiary legal considerations such as to include (but not be limited to) ‘time-stamps’.
8. How can Government and industry sensibly increase the security, quality and effectiveness of cyber security and digital offerings?
By building domestic capabilities that support local and international progress on the standardisation and growth of AI related solutions infrastructure (aka: a knowledge banking industry).
Lets imagine, there’s now say ‘two webs’ that are interoperable;
- One (1) is built upon existing business systems, where services such as those provided by international providers are distributed across the web on a technical basis — but are controlled centrally on a commercial basis — generally via one jurisdictional environment, to whom it must comply.
- The Second (2) is a variation of the business models employed, by the others technical apparatus; providing an alternative whereby both the technical distribution and ‘commercial’ distribution (business systems) are both ‘decentralised’; and is provided upon the basis that institutionally supportively apparatus that is required to allow this to occur; is decidedly supported, to do so.
In this second variation / iterative approach; the ability to produce and scale (commercialise) ‘digital offerings’ changes in the nature of how they’re developed and delivered.
As is apposed to the format of the first approach (1); the alternative (2) provides a means for legal entities to retain control over the informatics infrastructure that relates to them; whilst the app infrastructure, makes use of ‘semantic web tooling’ to form useful apparatus with the data that is collated as a consequence of underlying ‘social predicates’ defined in various parties informatics stores.
In both circumstances, data is in-turn able to interact with any compatible app (using W3C standards); yet in the second, this functional process can be performed without necessarily transmitting or sharing any 3rd party information to the app provider.
As such; the ecosystem acts to effectively shift the business rules; so that, the decision to share data is not based upon the definitive rules set-out by the app provider; but rather, those involved in defining rules in relation to the semantic relationships between cyber-informatics owners.
This is achieved by producing an ecosystem participating whose services as a ‘platform provider’ are delivered on behalf of legal entities (ie: natural & legal persons) as a ‘web of data’ provider. These providers in-turn participatory support the development and growth of permissive commons, much as existing ISPs support the management of IP Addresses & DNS services.
Open Data v3.0: Permissive Commons
_Why the open data movement needs a facelift, and how that might be done._medium.com
Tech for Permissive Commons
_How is a ‘permissive commons’ system made to work, and what does it provide, technically?_medium.com
These solutions frameworks in-turn require socio-economically supportive infrastructure including but not limited to: infrastructure project curation. This is in-turn illustrated by way of my many constituent articles on medium.
WebCivics
_Creative Works for a Knowledge Age_medium.com
The underlying Technical body of works that are aligned with my own (and indeed instrumental constituent pieces of it) are the subject of works internationally by an array of prominent technical and creative tenants of our global society; who all too-often in-turn, could benefit from better engagement with a nation state as to improve performance of deliverables.
9. Are there functions the Government currently performs that could be safely devolved to the private sector? What would the effect(s) be?
devolved? I argue the opportunity is about significantly evolution, which requires government involvement to bring about solutions that would in-turn improve the functions of government.
As is illustrated merely by the fact that it is a civilian who is now authoring this document.
Dissociative behaviours are not legally defensible, so why invest as to institute (& protect) them? In todays cyber domain, our borders are presently porous…
In the natural world, a scientific fact is that a ‘good ideas’ and ‘useful ‘inventions’, useful works; has no strict correlation to the application of a particular persons role role; in fact, systems that purport this type of disassociated conditional statement, and are consequentially, natively insecure.
I recently found myself writing an article i titled ‘re:inventing Einstein’ as to confer my thoughts about these sorts of ‘weird behaviours’.
Reality (and its relationship to causality) is in real-terms, extremely secure. Whilst artificial apparatus may be employed to pervert it, doing so only adds to circumstances of insecurity — irrespective of whether law-enforcement means exist to preserve ‘common-sense’ as does otherwise relate to law.
Just as the cause and effect of a biological or chemical reaction can be dependably relied upon; as can full and proper evaluations of situational conditions and social fabrics, as to review factors relating to causality.
Our societal rule book (law) is, by principles relating to law — intended to be rendered support and those doing it, should be made able to do it.
To achieve this,
The means to support domestic cryptographically enhanced ‘trust instruments’ are required; these are often called ‘credentials’ or ‘verifiable claims’.
As to support this ‘trust’ infrastructure, domestic cryptographic infrastructure is required (ie: root key certificate infrastructure), as to support ‘reality check — tech’ built on top of that infrastructure; whereby the ability for legal entities to make use of them — must be provided to all parties; whether it be for,
- A party invite (that might provide IoT Access to a secure building / venue); or for,
- A person to express, that they are ‘over 18’; or that they seek to be, and should be trusted for expressly defined purposes; by 3rd parties, for works (ie: those involving national security).
10. Is the regulatory environment for cyber security appropriate? Why or why not?
The difficulty in appropriating a well considered response is two fold.
Today, the internet and the tools built on top of it (ie: the web, web services and related functional properties) act in a particular way; which in-turn harbours specific challenges for domestic cyber security applications. It is far easier for small special interest groups to plug into this infrastructure; than it is for a more sophisticated policy related initiative, to be brought about.
In the USA there have been an array of activities going on, including but not limited to senate hearings. As was mentioned at one of these hearings the idea of an ‘information fiduciary’ was brought about; whilst noting therein, the jurisdictional differentiators between the US Marketplace / foundations and the means through which that infrastructure serves the American People, vs the means for infrastructure services to be provided as to similarly serve our own (and those of others world-wide).
A Grand Bargain to Make Tech Companies Trustworthy
_The information age has created new kinds of entities that have many of the trappings of fiduciaries-huge online…_www.theatlantic.com
Therein, whilst the Jack M. Balkin report “Information Fiduciaries and the First Amendment” provides a guide, that forms some parallels to the UK Work on Data Trusts, the implication about AI capabilities (& ‘knowledge’), in my mind extends beyond the levels of simply considering data / information.
Therein; the informatics structures form ‘knowledge emboidments’
However, given the tools to bring about alternative informatics structures does now technically exist — the regulatory environment is not fit for purpose, as to support its manufacture, commercialisation and widespread use of domestic infrastructure should the capacity to build it, be brought about.
Should it do so, i believe the outcomes could significantly improve,
- our socioeconomic environment,
- our cyber-security capabilities; and
- our means to innovate & commercialise, internationally, solutions frameworks that could be brought about,
from Australia, working with others overseas — should it be done well.
Therein, it’s not just about ‘regulatory environments’ but also the ability to best support / seek to ensure, the success of creative works by subject-matter-experts capable of doing the work involved — with others, in a complex market.
Once upon a time, a decision / declaration was made that a few groups, wanted to build the tools to fly to the moon.
President Kennedy’s Speech at Rice University Source: YouTube
The fact that someone got there first had as much to do with the creative works of those who did the work, as it did the fact that they were socially and economically supported to do the work, and build their ideas into solutions.
As with all major infrastructure projects, the economic support to do it is a part of the requirement. As this problem is similar in nature to the new ground, new science, new technological infrastructure required to take man to the moon for the first time; it is not reasonable to expect workable alternatives to our current international cyber ecology to be obtained freely via ‘open source developers’…
Ignorance is an array, not all of which are merely financial in nature, the creative works made by some persons, for whom it becomes part of their being, cannot be dishonestly replaced or redefined as to get the same outcome, by anyone, seeking to do so in such a way, for some benefit. This is part of how human consciousness works, which i think to be quantum mechanical in nature.
Theoretical relationship between social informatics systems and quantum physics — reality check &…
_Can you help figure out what is fact from what is fiction?_medium.com
Irrespectively of whether and how natural systems work, it seems most important not to work against it, but rather ensure the use of science and technology aids discovery and does not act or is not curated to act, as to defeat it.
Artificial Intelligence and Consciousness
_1._medium.com
11. What specific market incentives or regulatory changes should Government consider?
Something akin to an ‘Island Australia’ cyber-physical framework; whereby the informatics environments powering AI and advanced & ubiquitous socio-economic activities; be rendered a trust-worthy capability, to be operated domestically, that at least provides a domestic alternative.
This concept is not uniquely applied to Australia. It considers the idea that no-matter what happens internationally, whether there be a significant natural disaster or other significant problem; the needs of Australians can be maintained. This in-turn extends also to the ‘terms of use’ for Smart City / IoT infrastructure which is amongst the many ‘knowledge economy’ considerations of purposeful consideration, worldwide.
As such; I believe, there is an opportunity to produce a meaningful infrastructure project formed as a ‘public private partnership’ as to produce critical cyber infrastructure; working with government and internationally experts to bring about an alternative to the ‘status quo’, ASAP.
By doing so, we may find existing providers more interested in reviewing their stance on how they may better accommodate now long-standing issues.
To achieve this, the consideration is that there are critical requirements as to support the needs of humanity; as are distinct, on a legal basis, to those of artificial agents and actors.
This is in-turn objectively considered to be a ‘human centric’ approach, whereby the future of our natural world as is influenced by artificial tools and systems; that the responsibility for any and all actions, be squarely placed on human actors, both as individuals and as members of any and all groups.
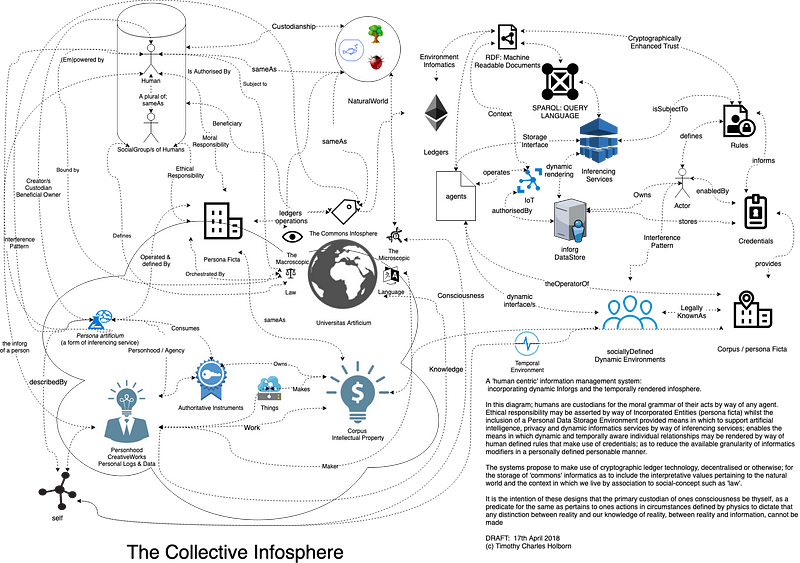
A Human Centric Infosphere diagram — as published here with a description therein.
Therein — whilst human actors maintain a moral responsibility, the ethical responsibility is in-turn rendered support by the mechanisms of group dynamics. Therein, the consideration of social dynamics illustrates that no one human being is able to do anything in isolation to all other human agents.
Thomas Thwaites: How I built a toaster — from scratch
Irrespective of any artificial concepts - a group who is engaging in activities that are knowingly wrong — is still made-up of individual humans. Wikipedia states that “The word “corporation” derives from corpus, the Latin word for body, or a “body of people”.
Yet today in many instances we have built a concept of ‘Corporate personhood’ that may be extended to support AI.
Could an artificial intelligence be considered a person under the law?
_Humans aren't the only people in society - at least according to the law. In the U.S., corporations have been given…_www.pbs.org
As our technology capabilities are going to perform various forms of ‘pervasive surveillance’ as required to make cyber- infrastructure work; it seems important that this be rendered an option, that be made ‘human centric’ (as distinct to (legal)‘people centric’; as such — qualities and concepts relating to personhood would apply; and the mechanical implications of emergent ‘software actors’ would in-turn be made to be legally associated to those responsible for them, in a legally viable manner.
Whether or not this approach can be made to work; without socioeconomic support required to undertake and make available alternatives that may make use of it, would be made to be a mute topic.
IMHO, humanity deserves safe options to be available, if nothing else.
12. What needs to be done so that cyber security is ‘built in’ to digital goods and services?
It is my belief that the ‘web of things’ solutions frameworks; which in-turn support a permissive authentication frameworks (ie: WebID-TLS — a TLS certificate with an in-built referenced URI / IRI — that can be employed to govern security of that device) which can in-turn support the ‘knowledge banking’ methodologies that have illustrated above. However there are aspects that relate to ‘semantic web’ and ‘permissive commons’ (per my articles) that are important part of ‘sense making’ my broader thoughts.
Andreessen Horowitz partner Peter Levine: The End of Cloud Computing
One such aspect to this is the manner in which the information topology can be decentralised as to incorporate use of many systems using linked-data. Therein, whilst a ‘Trusted knowledge bank’ plays a role; infrastructure would inter-operate with local systems in homes, for instance.
Therein, there are very different and distinct characteristics that are constituent design paradigms ‘built into’ my ‘knowledge banking’ methodology, that in-turn incorporates an array of related works in a particular way (including but not limited to the afore mentioned ‘solid’ project)and the consequential operational & functional attributes.
Therein — the ability, methodology and tooling to secure traditional ‘digitally connected goods and services’, is entirely different to my nuanced approach.
By producing infrastructure to support the means for a purchaser of a product to make use of that product without necessarily providing access to any other party; whilst supporting security via ‘knowledge banking infrastructure’, the options relating to how to achieve a better ‘cyber security outcome’ changes.
Should this series of considerations be considered to have merit, perhaps therefore consumer labelling that illustrates why people are buying into, would be useful for consumers seeking to make the right choice for them.
Alternatively, as the question may be responded to in consideration of how ‘things’ are made to work today — I’m not sure how to fix their Web 2: APIs, or the underlying functionality built into the devices in reliance of them.
13. How could we approach instilling better trust in ICT supply chains?
To start with; generally, there is a theoretical opportunity to evaluate the influences of particular natural persons and the influences they have on other things (ie: legal personalities); but this can only be achieved if the infrastructure exists, to support the identification and analysis of those persons activities, which should always be done unto law (lawfully).
Therein — even if the infrastructure existed, rule of law principles should ensure any ‘law enforcement requests’ are appropriated with fit and proper accountability & to good measure, rather than allowing; say,
a law enforcement officer to stalk their ex girlfriend… or a public servant to undermine a commercial pursuit, by misappropriating their powers.
In-turn; as illustrated previously, all of us are natural persons, no-matter what role we play. We all have bank accounts, this shift would in-turn uplift those types of considerations, to curate informatics.
I note: there are a number of other more sophisticated considerations, relating to any ‘built-in’ hardware or operating systems properties that could be weaponised; yet, i believe addressing this issue is something that may be done on an international basis, rather than seeking to shift the way these sorts of things occur more simply on a domestic basis.
Some of the underlying problems, relate to commercial attributes. So, the overarching consideration is that; if we change the nature of how greedy actors are motivated, then this in-turn can yield significant cyber-security benefits; as an inverse property of integrity measures.
As is consistent with the thinking and modelling of ‘permissive commons’ there is a capacity to issue verifiable claims or credentials, that in-turn make use of both signature informatics and ontological frameworks to support both human and machine readable statements in relation to ‘things’, people & concepts. Two examples of how prior works have evolved include Open Badge V2 spec and the Verifiable Claims working group, whilst noting the consideration that these ‘pieces’ are from my perspective, designed to support a specified form of ecosystems approach to informatics management.
Therein, the tooling would not only improve trust with ICT supply chains, but moreover — all supply chains.
14. How can Australian governments and private entities build a market of high quality cyber security professionals in Australia?
In my domain experience; i’ve found the ability to formerly engage (‘gainful employment’) to be an impossible mission, whilst it is seemingly the case that there are few ‘semantic web’ and ‘web science’ professionals in Australia, and fewer still employed to make use of their skills (if they have them) in this area.
Part of this problem is about local policies, others are about competitive behaviours that would not stand-up to fit and proper investigative capabilities. ‘rule of law’ for innovators, doesn’t really exist. Whilst there’s minor resources available for the poor in criminal matters, fewer still if they’re a victim of crime — there’s basically nothing available for commercial disputes.
Increasingly, areas of commercial issues incorporate criminal issues, whilst neither would be investigated without means to get help for what may be more simply classified to be a ‘commercial issue’… Therein — those who are making personal investments in innovation, are generally made to be poor, as a consequence of lack of available investment for ‘early stage ‘ideas’’, et.al.
The second point would be that, in my experience, there’s many around the world who have been similarly dedicated to these sorts of works; similar to my own, although with different skills-sets. The ability to identify where they can ‘fit in’; and how to get them into a position where they could be productively applied, (often at below ‘market cost’ for similar professionals operating here); is made to be yet another impossible task, in todays market.
I imagine the issue is similar to the advent of internet and the world-wide-web itself (alongside ‘bitcoin’); where the people in senior roles, did not feel it was a worthy field of pursuit to begin with, and as that was overtime found to be a falsely applied series of statements and agenda.
The next positional characteristic taken by the same people, as to control and be ‘uplifted into the positions’, that was previously suggested would not exist, is to improperly disassociate works from their origin sources, and build projects.
These behaviours damage trust and capacity. Australia, a relatively small (population) place, is known to be associated to an array of misleading statements and agendas in technology innovations of past.
Adam’s Platform, Bitcoin, others…
Source — Wikipedia: Diffusion of innovations
A problem that exists, irrespective of whether or not it’s able to be resolved; is that there is a practical series of real-world traits relating to innovation of any kind. At the very beginning, there is no commercial opportunity — so, the idea that those who are doing that work should reasonably be ‘unpaid’ doesn’t actually work — as to deliver commercial opportunities further down the road.
As such, the implications of whether we intend to produce valuable creative works in this country; or whether, we intend moreover to license or make use of them from overseas producers is a core constituent of how we support and preserve the ‘dignity’ of innovators, in an internationally competitive market.
The impact malfeasance has, from an intellectual property ‘provenance’ point of view; is that misappropriated ‘intellectual property holdings’, don’t stand-up to ‘international competitive forces’, overtime.
Patents are built upon priority dates, and they’re torn to pieces based on ‘prior art’ made by others, elsewhere, prior to the asserted Intellectual property claim.
This issue is of particular importance; when considering “artificial intelligence” or Semantic Web Graph Data capabilities as is operating on a widespread basis powering existing cyber-physical systems, throughout the world, inclusive to the implications that relate to Australia.
Whilst few are aware of full ‘graph technology capabilities’ the characteristics of them; kinda means, that although some individual operators believe this sort of long-term ‘politicking’ of recruitment practices, budget governance and commercial activity; is entirely fair game — in this particular field.
I fear that it’s fairly easy (technically) for a suitably equipped sophisticated actor, to identify and manipulate markets — making employment of such factors relating to, poor hygiene.
As such, matters of ‘inconvenience’ are of secondary concern.
On an ancillary basis, it appears that there is, in-turn, a cultural problem where others, who seek to support their lives, their families; are also encouraged to participate either actively or passively, as to keep the job they have (as they wait / seek, to be promoted), in wrong-doings towards others.
Therein, the production of ‘social graphs’ illustrating this, seems inevitable.
There are few individuals world-wide who are fully capable of arguing, in a sophisticated manner, about the nuanced decision making practices that relate to (artificial) intelligence infrastructure; and in-turn, these people have often struggled to survive and support their kids if they seek to serve, mankind. I believe the evidentiary inference of this predicament suggests there’s a bigger problem.
So, in my opinion — a good starting point may be to forge a special purpose vehicle that is specifically engineered to address this problem, and foster policy innovation for scalable growth.
Field of Dreams | “If You Build It, He Will Come”
In Australia, i think this incurs a requirement to expressly note various human rights considerations in the articles of association as to provide for the needs of a ‘fit for purpose’ legal entity, designed to be equipped to address fiduciary related problems in a manner that supports good decision making practices by company directors.
Should this structural practice method be appropriately employed by an appropriately equipped entity (inc. financial) i believe talent will come flocking.
15. Are there any barriers currently preventing the growth of the cyber insurance market in Australia? If so, how can they be addressed?
There’s a number of aspects to cyber-physical insurance markets, that are currently wholly unsupported or under supported.
Many of the traditional workplace related insurance products (inclusive to total permeant disability, health, income, etc) relates to traditional labour force environments; such as to more easily associate to an event where a labourer might be injured on a worksite in some physical manner; that stops them from being able to work.
In the cyber environment, risks more closely correlate to ‘intellectual property’ related activities — the useful employment of information as to pursue particular activities, often for commercial gain.
Therein;
- A person may work on something for a long-period of time, then provide derivative works to a potential investor or employer; who may in-turn, act to exploit that work and act to ensure no payment is made to its original producer — on the basis that they’ve got no financial capacity to legally pursue — what may otherwise be considered lawful obligations in relation to ‘fair terms’ in activities of trade.
- In other instances, say for example — ‘gaps in organised service delivery provisions, that intend to support’ public interests, spread across an array of departmental & contractor services;
- An issue may be identified by one agent, who may in-turn act to send that issue to another duty bound actor; who may in-turn,
- Send it to another, and this can go-on; as to act, in-effect,
- To fund an exhaustive and convoluted paper trail, that doesn’t actually resolve the underlying problem as was first alerted to government; and in so doing,
- Act to compound the cost put upon all participants in an informatics ecosystem.
These sorts of activity profiles present uninsurable risks to all participants.
The concept of a ‘knowledge banking industry’ is economically considered able to be built upon an array of cyber informationally financial, product offerings; including those that relate to insurance provisions, that in-turn use historical activity data to protect account (and policy) holders.
Yet this is not simply a primary engagement consideration.
Infrastructure, particularly IoT infrastructure; is bringing about a proliferation of devices and software services that can all be targeted.
To resolve the root issue of these problems; It is important that any one with the skills to improve the security of these devices / environments; are encouraged (and economically supported) to do so.
The way this can be supported to occur, is via micropayments infrastructure.
Therein, a single ‘fix’ to a piece of software, operating thousands, tens of thousands or even millions of lights or locks — could articulate via micropayments — to easily provide for a few hours work; by some talented individual and any testers.
Yet to do so, this means there is a need to produce ‘digital identity’ and KYC/KYCC/AML.
NB; IPv6 supports an array of functional security characteristics IPv4 does not.
The opportunity framework of producing lawfully relatable and queryable graphs, changes the vast user topology so that those who are opaque become far more prominent, than those who are operating within a framework that is intended & supported to preserve dignity; and through that lens,
offer the means for cyber-insurance products to manage risk, and in-turn produce new insurance related products that can address other issues, like innovation activity insurance — building off provenance, to insure against bad actors.
16. How can high-volume, low-sophistication malicious activity targeting Australia be reduced?
Interestingly enough, the first application considered by ‘satoshi’ was ‘pay to send email’. https://www.mail-archive.com/cryptography@metzdowd.com/msg10162.html Yet this is still not something that’s available; as a consequence of a lack of infrastructure support for it.
With respect to traditional attacks on machines — there are two major avenues through which malicious occur;
- Websites
Micropayments systems are able to offer a commercial alternative to advertising revenue, which attends to means that can be employed to resolve (a); whilst emails, have an ability to use a social graph (should one be deployed as to support individuals needs) to better discern between the activities of ‘real world actors’ and those that have no known affiliation to a real-world actor. Whilst this is currently supported to some-degree via proprietary products & platforms; the hope, would be that it is understandably beneficial for a commercial topology to be made available that does not bind a persons social-relations and activities, to the use of a particular commercial platform (ie: linkedin, facebook, google, skype, telegram, AusPost, etc.).
Yet this is not the only type of attack-vector employed through the use of Cyber Infrastructure.
There are both institutional attacks (ie: false statements made in database records) and public / social attack vectors.
A W3C group has been working to define the scope of these problems. below is a table that has been produced by them.
Please see license and contribution details at the bottom
Audience & Accuracy Grid
[1] Direct. Delivery aligns with harm, with content delivered to the person harmed (the target). Blocking helps.
[2] Content delivered to target and others. Requires audience.
[3] Indirect. Content delivered to others and effective without target receiving it. Blocking does not help.
Attack depends on delivery to target
Attack depends on delivery to others
[A] High Accuracy. Can be effective while being essentially true.
Stalking
Threatening
Harassing
Unwanted attention
Unwanted intimacy
Triggering (revulsion, phobias, epilepsy, PTSD response, depression, eating disorders, self-harm, suicide, bad habits, addictions, …)
Gaslighting
Demoralizing
Spoiling fun
Kink-shaming/slut-shaming
Narrative Spoilers
Wasting time (sealioning)
Cliffhangers
Provocation to platform-prohibited behavior
Provocation to careless speech
Blackmail
Bypassing decisions by guardians for age-appropriate content (for children)
Speaking truth to power (may harm powerful, or people perceived as powerful in context)
Excessive volume of public comments
Mocking to their face
Expression of hope that harm comes to the person
Demanding action before removing publicly shaming content
Shifting tone of a space to be hostile to target
Dangerous challenge memes
Spreading divisive (consensus-resistant) content.
Doxing (publication of home address, phone number, email, identities of family members/friends, medical history…)
Copyright Infringement
Stealing jokes / attribution failure
Outing
Leaks from an organisation
Leaks of personal communication
Sexual images/recordings without subject’s consent
Revealing details of intimate relationship
Reporting prohibited or dubious behaviour
Advance rebuttal
Asking that someone be ignored/excluded
Mocking behind their back (including with photos/memes)
SEO of harmful content
Publication of statements in a different context (eg years later)
Signal flaring (drawing unwanted attention)
[B] Accuracy varies. Some misleading often necessary to be effective
Advertising
Spam (advertising in a non-ad space)
Insults
Raising anxiety
Raising outrage
Clickbait
Dark patterns (in UI design)
Dunking (being mean mostly for the audience)
Dog piling
Playing the victim
Publicly threatening one person to intimidate or silence a group.
Incitement to genocide
Recruitment to causes and organisations opposed to target
Badmouthing/gossip
Stochastic terrorism
Threatening target’s medical provider
Harassing target’s spouse, friends, and family, linked to from target’s social media profiles
[C] Low Accuracy. Attack depends on receiver being convinced to believe something false
Phishing
Cat-fishing
Financial fraud
Demonstrating someone’s gullibility
Credibility hijacking (getting someone to share false content)
Visibly ignoring
Intentional misreading
Faked stunt challenges
Unrecognised Satire
Hoaxes (often unclear who is the target)
Click farms
Brigading (secretly coordinated crowd)
Impersonation / identity theft
Slander
SWATing
False complaints to target’s employer or professional organisation.
False complaints to Child Protective Services aimed at target’s children
Some other aspects of these attacks that might be helpful to visually identify:
Which attacks are often accidental and might be reduced by education or warnings
Severity of individual attacks, prevalence, or harm done in total worldwide
Which attacks are illegal in various jurisdictions
Which attacks are gradual, requiring a sequence of steps over time, and so might be mitigated by being cut off early, vs happening all at once
Which attacks are perpetrated by people familiar to the target vs strangers
Population characteristics of average targets and perpetrators of each attack
This document was initially drafted by Sandro Hawke (sandro@w3.org) for possible use by W3C groups, including Credible Web CG and Social Web Incubator CG. Short comments are welcome here or on the announcement tweet. Please structure longer comments as new issues on this github repo.
License: CC0 — Creative Commons. By suggesting any changes to this document, you are agreeing to license your suggested text under this license. Earlier version mistakenly had a more restrictive license; if you contributed under that license and object to CC0, please undo your edit.
Thanks to folks who have been helping! If you’d like to be credited, put your name here (with link/handle if you want): Irene Knapp, Cidney Hamilton (cidneyhamilton.com)
Adding to the every extending creative works of wrong-doers; there’s now also other modern risks emerging in a manner that could not have happened without a cyber environment; such as to include (but not be limited to) AI Generated videos depicting others to do or say things that do not in reality, at all relate to them.
Which in-turn also relates to commercial applications of the same technology to use AI to for ‘personalised messages’ that makes use of graph information to seek a particular response type;
The manifest reality that relates — and can be attributed to these forms of attack-vectors; is specifically related to the behavioural attributes of particular individuals and the groups they work with. Therein — the current profile and capacity to define particular query sets, that can otherwise be relatively easily ‘written once and used anywhere’ (using semantic web ecosystems); do not currently, have any infrastructure solutions that can make them easily able to be deployed for more dignified purposes.
There is a technical capacity to identify and attribute ‘space time data’ about a person, which could in-turn be employed by cyber-physical systems in relation to them, to distinguish when it is them; and when it is not. To do so, would in-turn require a means to store that information — by them, for them.
As such; the engineering characteristics of how infrastructure operates today, is the cause of a hostile environment, where false assumptions can easily be made and result in wilfully (yet erroneously) delivered outcomes put upon others; on a basis, of ‘false beliefs’, made profitable via ad-revenue.
This ‘informatics built’ commercially funded; forms ‘interference pattern’ like cyber-attack vector, forming a graph able (and likely predictable) array of

responsibilities relating to causality between the instigation of an event; and the effect of it
ie: the interference graph above notes 2 agents — imagine the same sort of thing overtime involving thousands of data-points / intersections / ripples.
The way that’s in-turn employed to cause effects to those involved in it, alongside those who are affected consequentially overtime (temporally).
In-turn, whilst there is a cyber means to make use of graph infrastructure to review an evaluate the ‘ripple effects’ the means to do so is compromised if the dataset made available is purposefully incomplete.
The way to resolve this issue, is by ensuring relevant capable service provisions are made available for all legal actors, with particular regard for the now underserved natural persons; who are instrumentally involved in all activities that relate in any way to cyber-security.
17. What changes can Government make to create a hostile environment for malicious cyber actors?
The simple means to do so; is by providing infrastructure that is designed to most benefit honest actors who are committed to law abiding activities; and seek protection from those who do not share that commitment. I think its fairly safe to assume most malicious actors do so for economic gain, so if it is economically disadvantageous to be malicious, behaviours will be influenced.
Noting: The definition of ‘malicious cyber actors’ isn’t really binary in nature.
Arguably, those who provide Australians products and services that governed the use and creation of ‘intellectual property’ upon foreign laws, and related incumbent implications; aren’t really good actors either, yet their decisions affect billions — whilst the actions of a few, can cause far more instrumental harm — to a few, or to entire economies.
‘White collar crimes’, such as those executed by commercial / financial / legal professionals; are often carried out through the meaningful employment of cyber-physical systems.
It’s not all in ‘print era’ activities — they’re not performing those criminal activities entirely ‘off line’…
So, the answer really is — provide the infrastructure required to support those who support ‘rule of law’, and make sure those actors who do support ‘rule of law’ have rapid remedy available & made accessible to them; so that there’s no excuses and no ripple effects, caused by bad actors, the most professional of such; have complex systems to support their criminal (whilst it’s only criminal if that’s found to be the case in a court of law) works.
18. How can governments and private entities better proactively identify and remediate cyber risks on essential private networks?
If there is infrastructure to support the entities and their relations to other entities; in a permissively networkable ‘social’ environment, then identification becomes much easier.
To achieve this; consider for instance, if the decisions were not about ‘cyber infrastructure’ but rather ‘physical infrastructure’.
Does a business require an office? Do their employees require shelter? Should the shelter (homes) of employees be owned by government or by their employer?
Today — we’ve got lots of cyber ‘shelters’ (offices) for legal personalities (gov, businesses, etc.) but we’ve got no infrastructure for natural legal entities, citizens.
in working to solve that problem,
a choice needs to be made about who is going to ‘own’ those ‘shelters’.
- It’s certainly easier to ask and/or resolve outstanding issues that would provide the means for Google, Apple & Microsoft to build that social infrastructure (cyber-shelters); but.
- Their services platforms do not have ‘terms of service agreements’ that say ‘Choice of Law (Some jurisdictional territory in) Commonwealth of Australia; and frankly,
- They’re well down the track of providing these sorts of infrastructure solutions, with the absence of AU built alternatives; noting,
- They’ve got billions of users world-wide, and we’ve only got a tens of millions of citizens — few of whom, care — or have any grounded honest level of trust for gov.
The implications are not simply domestic (au) in nature, yet it may well be the case that Australia has a level of ‘tech debt’ that may be more difficult to fix.
So, the answer appears to be, that if we want to turn this situation around, then it may be a ‘nation building exercise’ that may be best done with others.
and if we do so,
It would be a substantial project, requiring specialist expertise of particular persons, who in-turn require a supportive environment to do the job.
19. What private networks should be considered critical systems that need stronger cyber defences?
If private networks build their own ‘semantic’ ‘cyber’ infrastructure solutions to clearly delineate and support informatics between various interactions with other agents; it is therefore in their interest, that each natural person involved is equipped, beyond their own capacities alone; to be supported as individuals in informatics environments that provides them the capacity, to better be supported by analytical solutions that support trusted environments.
IF a school or local council wants to employ an external contractor;
- do they have a police & working with children check?
- do they have the trade qualifications to ensure the work they do, is insurable?
These sorts of functions can be carried out by the contractor and stored by them, to be used in connection to the creation of a ‘job requests’, Appointment (calendar entry) and (IoT) access keys; alongside the means to streamline payments & accounting.
The consequential logs created by permissively curated ‘informatics solutions’ can vastly improve the means for private organisations to lower operational risks; and,
- Perform ‘root cause analysis’ when a catastrophe occurs; which in-turn,
- Translates to insurable risks; and,
- Improved economic performance / operational efficiencies.
The other ‘cyber asset’ aspect; is the potential cost to actors for data-breaches.
- By employing means that permissively link data-assets stored by their moral owner / custodian; The volume of,
- ‘stored social-network data’ about ecosystems, is reduced; Furthermore,
- As the ‘API’ (application programming interface) is self-describing, the implementation cost to achieve this outcome is far less than traditional API Alternatives.
In-effect, the informatics environment becomes more generic as to be controlled by permissive instruments rather than software vendors or their products.
Therein also; An aspect of particular concern is those that relate to children, in all parts of their lives.
Increasingly, modern interfaces require / desire biometric interfaces; such as, face or voice recognition. As such, knowing from a telecommunications point of view; existing ‘gov network’ infrastructure does today exist, the question that is brought about, is how to form a permissive framework that precludes visibility of activities by children, to those who are permissively defined to be part of their (parentally supervised) social network.
The ability to target a person by way of their children, is an unwanted threat scenario that is moreover well known by PEPs amongst others.
Therefore; publicly attributed assets relating to children, is an unwanted functional characteristic, that’s now all too common; from early years, to those later on.
Infrastructure, and a series of policies need to be formed to protect children.
This in-turn also needs to consider how online infrastructure is made to work in relation to them broadly; which is one of many similarly sensitive use-cases.
20. What funding models should Government explore for any additional protections provided to the community?
One of the mission model canvas diagrams: See Source
PPP and BOT related infrastructure investment models, that are designed to support objective outcomes. A more easily illustrated model is that which is provided by Steve Blank called a ‘mission model canvas’.
As is a constituent response method to forming trust with government, the means for consumers to easily make complaints and to have those complaints fully addressed; seemingly also requires an innovative funding model.
One idea i have — is to use financial metrics and associate those metrics to criminal penalty points if asserted claims are found to be knowingly false.
Therein, the concept is that a citizen, commercial entity or consumer may be entitled to make a complaint about a practice method applied to them, that is not consistent with law or related legitimate policies.
Yet the act of doing so, may in some cases be based on false accusations and/or intended acts of malfeasance and wrongdoing, as to pervert the course of justice and/or misappropriate law — as to cause others injury.
The problem this appears to be closely aligned to, is the apparent cost and trustworthiness relating the person making a claim that should be considered, in good faith, to warrant investigation and resolution — in the interests of ‘good government’ whilst protecting the interests of taxpayers from unfair and/or corrupt behaviours by ecosystem participants.
Now therefore;
- If there was a mechanism that accumulated the cost of investigations in dollar terms, that in-turn associate to penalty units (ie; 1 penalty unit = ~$210?) then, there is a costing that is applied to the undertaking of investigations; that may be put upon whomsoever be found to have performed wrong-doings whilst seeking the protection by way of public funds,
- Be applied to the ‘knowledge economy’ act(s) of requiring public expenditure to resource a resolution.
The second factor is that the means to lawfully undertake activities of a fit and proper purpose, must be provided on a basis that would make it lawfully reasonable to expect people to do so.
Amongst the many areas this consideration applies to; one of particular concern, are the circumstances of young people, particularly those seeking further tertiary education, which is presently illustrated to have very poor mechanisms for government support and high levels of prostitution and/or online “arrangements” in manners that have fewer protections than brothels.
Universitas Doctrina et Sapientiae
_Re:defining the business systems for the tertiary eduction sector._medium.com
A full and genuine evaluation of our tertiary sector and economic affiliates (ie: Austudy, cost of living, etc.) should be undertaken on a basis of evaluating ‘national security’ implications (and opportunities) of the few dollars saved by having limited maintenance funds (NB: UK example) made available to domestic students; to such low levels, which is a problem that in-turn made worse by the ‘free work’ trends, and a lack of available jobs (although stats aren’t spoken about readily in the news, with respect to very similar considerations — more broadly).
21. What are the constraints to information sharing between Government and industry on cyber threats and vulnerabilities?
Current ‘legal infrastructure’ seemingly acts to sacrifice ‘dignity’ through the texts designated to support ‘privacy’ considerations. Making matters worse, related dynamics seek the sole holder of important records to be institutional stored by the provider of a product or service and that documents be privately considered to be an institutional ‘source of truth’ for decision makers.
Whilst failures may lead to significant injury to the ‘data subject’ (‘consumer’); this is seemingly responded to be limiting the capacity to seek and perform compensatory acts where harmful behaviours are exacted upon others upon a basis of false (3rd party) assumptions. Amongst the many qualities this circumstantial situation brings about; are those that include a basis for reasonable confusion about when a consumer should seek to be made aware and/or seek amendments under the privacy act, or the FOI Act.
Compounding problems; the responding agency may not be cooperate at all, or not at all in a timely manner; whilst ignorant of data available internationally, that may in-turn very well illustrate ‘inconvenient facts’.
This manifestly acts to form unwanted attack vectors upon our society, our democracy. Should this be revised;
The considerations that could be brought to bare, could incorporate both the meaningful utility of an ‘electronic search warrant’ and the means to support semantic infrastructure that is ‘built-in’ that supports ‘permissive commons’;
or,
In other words;
“The ability for non-identifiable derivative materials (from audible sources) to produce derivative knowledge-class assets, that can significantly improve ‘situational awareness’.”
To achieve this, the underlying concept of ensuring natural persons are all accounted for;
as to ensure,
- There is not, what may be illegally employed, wilful differentiation between persons employed by government acting outside of the law; and/or,
- The terms of classified responsibilities; and,
- Those of the persons to whom they may target in the discharge of their powers, as an employee or agent, for a public institution (or related entity) of lawful trust.
22. To what extent do you agree that a lack of cyber awareness drives poor consumer choices and/or market offerings?
Q: Would ontological (OWL / RDF / Semantic Web) infrastructure support vastly improved product and service labelling?
A: Yes. It absolutely would.
The confluence of international works that act to chart the entire supply chain (ie: from farms to plate) can not only identify persons who may have consumed contaminated products, but also act to identify contaminations that would otherwise be vastly more difficult to resource assertions about.
Q: Would consumers (inclusive to government) care if they understood the vast capabilities that are able to be employed by sophisticated international actors?
A: Probably.
but what can they do about it if the situation is considered to be ‘acceptable’ by their government; and as a consequence of that,
no alternatives are available for them to employ to better their lives.
Q: Do the current ‘web 2.0’ solutions exhibit significant commercial barriers?
A: Yes.
That was the case even for the businesses who grew globally, they were funded to do so; even though there was no viable underlying business model to turn a profit and still today, some still run at a loss.
This is considered to be ‘unacceptable’ in our domestic market, which has an array of significant implications on what it is that’s created, to grow over decades.
Q: Do alternative solutions exhibit the same sort of economic ecosystems (business systems)?
A: No. they do not.
this doesn’t mean they can be created for free, by people who are expected to do so — by finding some other way to support themselves whilst doing the free work; that will most likely be commercialised by an existing sophisticated actor, without attribution to the original creators of it.
Q: Is the problem about cyber-security?
A: depends on the intepretation.
I like rule of law. I think we have a viable opportunity to produce tools to support it, but i’m not convinced its something that is considered ‘desirable’ for reasons that are beyond me; and so, there’s an array of questions this in-turn brings about, that i think is only necessary due to lack of comprehension / understanding, and that this is a product of poor investment choices.
People learn about things, by doing them.
I don’t think much time has been spent on doing any form of work that is intended to support the means to make a ‘knowledge banking industry’ (built on semantic infrastructure) domestically, other than the work that has been carried out by me and those that have done their best to help, without available funding. So, consequentially — the level of ‘semantic web comprehension’ appears to be very low; and to compound this fact,
there are material implications to the production of apparatus required for the business systems creation process, alongside other derivative artefacts required to produce good and useful legal / legislative environments; as is now required,
to support international projects, such as the libra association’s works & related implications.
23. How can an increased consumer focus on cyber security benefit Australian businesses who create cyber secure products?
Perhaps there is a very difficult and innovative process required to assist with the instrumentation of what should be publicly discussed, and what should be kept private and/or under non-disclosure terms (or indeed also classified).
Assuming the focus provides meaningful support for the needs of individuals (personhood); a (vastly) improved focus to cyber security is likely to improve terms of trade for good actors, whilst improving means to mitigate the risks (and support the means for government to act — whether criminally and/or via heath / mental health programs) related to bad actors.
‘my word, is my bond’.
Well today, there’s services like siri that can track that sort of thing…
Yet, as i’ve tried to communicate — the underlying technology platform powering infrastructure services like ‘siri’ is currently internationally governed, and we have no good local options. If we are to work domestically with international experts to build alternatives, we earn and maintain the right to be trustworthy.
24. What are examples of best practice behaviour change campaigns or measures? How did they achieve scale and how were they evaluated?
So, a university taught concept was ‘mind position’, whereby — if asked what brand you first think of in relation to the term ‘cola’ — most people pick ‘one or the other’…
Another example would be ‘norm’, or ‘live. Be in It.’ In this case, substantive funds were provided, alongside significant use of broadcast space provided for community services.
Should — my broader considerations be considered to ‘have merit’; then i suggest that we,
- undertake an ‘entity evaluation’ activity be undertaken to consider the cyber-physical relationships that otherwise exist in the physical market-share; and then,
- Attribute what cyber-infrastructure capabilities those actors facilitate in society and upon what terms; through that,
- The ability to discern an ‘entity analysis’ graph framework can be formed; as to,
act as to Inform an approach that would in-turn seek to forge an ecosystem that supports express functional characteristics, that can in-turn grow, and be build upon.
25. Would you like to see cyber security features prioritised in products and services?
Very much so. Yet the practice method to do so, means addressing what most could oversimplify as ‘digital identity infrastructure’ that i call ‘inforgs’ and ‘knowledge banking infrastructure’, which is overall — a big job, to do right.
But i am deeply concerned the approach may well be architecturally defined as to be made necessarily insecure; despite other options being available, for the brave.
26. Is there anything else that Government should consider in developing Australia’s 2020 Cyber Security Strategy?
There are an array of ‘moral virtues’ and related attributes to human beings, that are broadly not codified well at all.
As a consequence, systems can act to harm good actors, whilst providing meaningful assistance to bad actors — in ways, that no later enquiry alone can resolve. These personal attributes, that relate to what it is to be human — is considered by some, to be of most importance overall.
The ideals of being Australian, is IMHO not about who someones parents or family are; or where they grew-up, or what book they were taught in religious studies; or whether, they were poor, wealthy — well cared for, or neglected. Yet this may all change very rapidly, depending on how we forge tools for cyberspace.
There are so many facets that go into the enormously complex socio-consciously derived internal biological algorithms, that poorly defined ‘classifications’ — can act to do enormous harm; and potentially sell our intellectual capacities as low-cost or cost-free commodities to sophisticated overseas actors; some of whom,
have more capacity to perform ‘knowledge enquiries’ than any Australian Entity.
People use google every day, typing queries into its ‘search box’ as to get the records relating to that query, in milliseconds, from around the world; without thinking about what that tooling ecosystem can do, for other purposes.
If we truely care about cyber security, then it’s imperative we build the infrastructure apparatus required to provide careful material support for our principles, built on rule of law.
In todays market, it is likely that there is far more economic flow being gainfully attributed to consultants and property administrators (ie: hubs) than is attributed to innovators, creators — doers; those people, who’ve been thinking about some problem for a really long time, and have sought to do something to build useful derivatives from their ‘ideas’.
This in-turn relates also to consumption of ‘ideas’ (a broadly used term) to attract and define investments, incrementally, across multiple sophisticated markets.
- The problem in-turn becomes, that those who have positions of influence in large corporates, generally don’t innovate as to start with an idea; but rather, harvest from the market opportunities, which once sufficiently evolved by others — can substantiate large-scale defined investment activities; and then,
The problems attributable to this series of commercial-social behaviours, noting
- that those creating the works are often doing so outside of corporate environments at their own expense; and,
- do not have the benefits, both socially and economically supported enterprise agents do; is that,
There is a consequential decoupling between the intrinsic knowledge equity formed by creators / creative workers defining ‘ideas’; and those who are ‘empowered’ to exploit those works.
This in-turn often leads to significant lack of innate knowledge about the topical endeavour.
Whilst the proposed ‘knowledge banking method’ provides a means to take the cost burdens away from government expenditure (ie: human services budgets); and bring about insurable, and domestic capabilities for risk related governance issues brought about; there is seemingly,
- a series of inferences that present a problem that those who seek to solve the underlying ‘trust’ issues; have been knowingly dishonest, and
- seek others to trust them preferentially on that basis; in perpetuity.
This in-turn has real-world consequences, that need to be addressed; far beyond the realms simply defined by semantic technology inferencing capabilities.
In previous eras of significant change; this problem might be likened to, the idea that someone is expressly advising a doctor that there’s a thing called ‘penicillin’ that exists — but due to the fact that the person alerting the doctor of it not being trusted — the doctor continues going about cutting off legs and otherwise dealing with medical issues without it.
Thereafter the question of whether the action was of wilful negligence and whether the one-legged man should pay the cost, becomes relevant.
Perhaps it was the case in the old days ‘plausible deniability’ was far more easily achieved; but the question today may moreover be — when is it appropriate?
Is it intended to perform a series of curated works as to ensure that doctor could say, they found the cure themselves and all other things relating to reality — should be extinguished? how about sales people, rather than doctors, or teachers, or investors… et.al.
I’ve previously asked the W3C if they could / would remove all my list activity from their logs, but told me that for policy reasons — they won’t / can’t do that.
Therein, my point is that whilst domestic policies may be ‘misapplied’ to ‘misappropriate fictions’, as nonfiction, this is unlikely to be provided any effective level of support internationally with AI systems for our worlds population (7.5Bn humans + biosphere considerations).
Therein also; are considerations relating to the concept of restraint.
A highly skilled person is expected not to use excessive force when dealing with an attacker whose actions are intended to cause harm; or do so, on the basis of false information, still causing harm.
In my observations the level of ‘hygiene’ wilfully supported by government, is ‘not healthy’ at all..
NB: remarkable changes have occurred, some related both by timing, activities, communications, alerts and considerations made by my own works seeking various changes overtime…
Whilst semantic graph technology can be used to perform (temporal) ‘root cause analysis’, It seems contrary to the interests of government to financially support malfeasances; particularly where,
it is in the national interest to ensure ‘consumers’ (citizens) trust domestic services over an above those of internationally provided vendors (and/or persons) — particularly with respect to life threatening events.
From experience; it’s fairly undignified to see a uniform (and its corresponding oath) misappropriated, only to struggle through the repercussions and when reality bites — have them defended for wrong-doings — as a consequence of their wearing a uniform; and the inconvenient nature the misuse of it — as to cause meaningful injury to others, is perceived to deserve (systemic) protections. Indeed my works with Military, UN & Law Enforcement Leaders simply illustrate to me; that this is not at all, something i should take personally — as they can tell me their stories, which doesn’t really help..
the problem is,
Government may well have in delivering upon its duty to support cyber security, is their means to ensure its employees are bound to the duties and obligations of their roles unto law.
The most remarkable of all circumstances i remember, was looking at the eyes of a prominent Australian whose leadership work in the UN is so highly regarded; as he spoke of his work in attending to the issue that some of those he served with, operated with impunity for sexually assaulting children.
Where he had previously noted to me and others in a conference i held in 2017 (per video aside), that the meaning of his role, of what it is he did; in service to his nation, our world — was sullied in that way.
This is the same for any ‘uniformed officer’ whose moral standing is given no contrast to those who commit offences in the use of them, including those that would result in life penalties, which i most certainly concur with those others whom i look-up to, agreeably.
Noting therein — whilst not all acts are materially so horrendous, the act of providing systemic support for wrong-doers — acts to deny the best individuals, the respect they deserve for having done hard jobs, in the service of our nation, our virtues, our people.
The practice of torturing an individual or an organisation, by way of (a) “thousand cuts”, is not ok.
Where circumstances provide for access to justice; or as is otherwise defined by various legal instruments, the combination of technology and its use to support rule of law.
Therein — i’m not talking about the idea that someone goes over the speed-limit for a few moments, and are automagically sent a fine — rather, there are serious harms that are committed against people, in a manner curated by the public service; and from my experience — i don’t care for their tears in telling me their sorry about it. So, if government wants to be trusted by the people, it must use technology to be trustworthy; the alternative is — to build a fake-news system that meaningfully disorientates the population as to ensure they’re ability to make educated decisions is made mute; alongside the basic underlying foundations of our democracy, via engineered gov projects.
There is an opportunity to uplift the age of mankind from this environment where dissociative disorders are designed to play such a significant role in peoples lives; to one, that uplifts our information age foundations — to an era of a ‘knowledge age’.
A Future Knowledge Age
_A Future that is about engineering for an emergent knowledge age._medium.com
A Knowledge Age, that makes full use of AI in a ‘human centric’ manner, supported by institutional infrstructure & appropriate laws; Where it is not about whether or not we acknowledge that data about anything probably exists; but rather; the engineering of socio-economic cyber-physical systems, designed to perform well with it.
I don’t know who the Australians, considered good, are, who would want to be known for wilfully supporting criminal activity, wrong-doing, wilful, negligent and unlawful harms against others.
I don’t think any parliamentarian has any lawful capacity; to stand up in parliament and state that it is their intention to harm their constituents.
This is the sort of conduct within Australia, that should be distinguished from the constituent aspects of a person, promoted to be a leader. Where the technological means exist to support the needs of good citizens; Wrong-doing should not be supported as to engender wealth, or act to plunder opportunities gained from others by such means.
I don’t know who, in Australia would ever want to be associated to supporting wrongs against others in Australia, as a means to engender international trade upon fair terms. Indeed — i suspect, it is a cause of enormous additional risk, that in-turn impacts GDP.
It is my view; that the inconvenience brought upon the few by reengineering systems to perform their intended tasks with ‘good hygiene’, would have a far greater impact upon us all, than any one could possibly imagine.
- I think it’s like ripping off the bandages to get the burns surgery that was required, but said to ‘not be so much of a problem’, until, they got into & onto it.
- I believe the overall cost of rendering institutional support for ‘delusional representations’ to be in the territory of hundreds of billions of dollars.
GDP doesn’t improve by the work of people struggling to survive; it overall improves, when the vast majority can thrive and produce works that can be sold to solve problems overseas. Society flourishes when its best equipped to solve problems, whether those problems be homelessness, environment, health — a cure for ailments such as cancer or the means to address the potential of crispr babies.
Conversely, if an agenda to do the opposite is undertaken as to stymie the production and/or availability of reliable ‘knowledge assets’ domestically, then the opposite is true — and i do not know how that could be internationally competitive, as to both sustain and enhance the quality of life for Australians.
Therein, for instance, the lack of available statistics about significant social problems, is a cyber-security risk.
The decision to build ‘knowledge age infrastructure’ as seemingly commenced in 1945, from a political chamber point of view, should be an easy vote to make.
How else, should it be reasonably considered that we live in a democracy if there are enormous ‘information age’ problems that act to pervert the ability for people to meaningfully engage & be made able to vote about matters of importance to them.
Tooling for Democracies
_Democracies are build upon the principle concept that citizens are represented by elected members. Knowledge Banks help…_medium.com
National Communications (Telecommunications Infrastructure) Security
Much like similar sorts of issues with email, the capacity to spam persons over the telecommunications network is a cyber security issue. Factors relating to this issue; include,
- VoIP (phone number) Spoofing
- In-Ability to identify group caller (ie: ‘government’ as apposed to ‘private caller’.
- In-Ability to have a code or some form of 2nd factor auth for gov interactions. (Unofficial calls)
- In-ability to resolve telecommunications attacks affecting citizens in a timely manner.
A Mobile Phone Number, is now used for 2nd factor authentication. The inability to resolve attacks no-longer simply means someone should change their number and go through their address-book to advise people of their new number (an act that in itself is likely to provide an attacker the details of the new number anyway); but also, all of the online services, including those provided by GOV requires a person to have access to the phone number they have registered.
The current ‘state of play’ for cyber-security measures that assist citizens, is currently very poor.
The entire purpose of forming ‘cyber-physical — system of government’ (as distinct to simply ‘government’) infrastructure; provides a significant means to lower the attack surface internationally, whilst providing domestic capabilities to protect national interests & our democracy.
To support this type of initiative,
- There is a meaningful opportunity to look at first deploying frameworks in tertiary education communities to both address factors that are acting to cause far broader problems; as well as providing a means to incubate early commercialisation of innovative works, prior to broader use.
- The NBN can be made to be critical infrastructure in a manner that provides seperate network topologies that can serve the needs of various community groups and service qualities required. This form of thinking includes considerations that relate to;
- The delivery of national (UHD compatible) media infrastructure that is competitive to international alternatives
- The delivery of dignity enhancing & privacy preserving infrastructure for Australian Children
- The delivery of critical communications infrastructure for those who cannot afford it
- The means to ensure access to critical ‘emergency service — management infrastructure’ free from monthly costs (and international influence)
- A number of legislative instruments will need to be formed overtime; as to provide the necessary protections for citizens in relation to institutionally provided services that will know more about them, than they know about themselves, or anyone (or anything) else due to human factors.
Human beings have an array of ‘ontological’ traits that are not supported by AI at present which needs work; but will never be a series of qualities that relate to anything other than being human.
It is governments responsibility, inclusive to cyber-security infrastructure, to protect those qualities from attack; that may be caused by humans, but should not be supported by any legal personality, but there is a viable ecosystems approach that can be developed and deployed, to Advance Australia Fair.